AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : You have created a VPC with the IP addresses, now after months you found that, this VPC is not enough. You need the VPC with at least IP
addresses. So what you have to do upgrade the VPC with 32 IP addresses.

1. Change the CIDR block and add new 16 IP addresses.
2. Delete the CIDR block and add all 32 IP addresses again.
3. More than 16 IP addresses are not supported in VPC
4. Delete the VPC, and then create a new, larger VPC
Correct Answer : 4
Explanation: You can assign a single CIDR block to a VPC. The allowed block size is between a /28 netmask and /16 netmask. In other words, the VPC can contain from 16 to
65,536 IP addresses. You can't change the size of a VPC after you create it. If your VPC is too small to meet your needs, you must terminate all the instances in the VPC, delete the
VPC, and then create a new, larger VPC.
Question : Consider the below scenerio.
A VPC with CIDR block 10.0.0.0/16
A subnet in that VPC with CIDR block 10.0.1.0/24
Instances running in that subnet with IP addresses 10.0.1.4 and 10.0.1.5
On-premises host networks using CIDR blocks 10.0.37.0/24 and 10.1.38.0/24
Select the correct statement from below.
1. When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, the traffic is dropped
2. When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, can talk
3. When those instances in the VPC try to talk to hosts in the 10.1.38.0/24 address space, the traffic is dropped
4. Only 1 and 3
5. Only 2 and 3
Correct Answers: 1
Explanation: You can optionally set up a connection between your VPC and your corporate or home network. If you have an IP address prefix in your VPC that overlaps with
one of your networks' prefixes, any traffic to the network's prefix is dropped. For example, let's say that you have the following:
A VPC with CIDR block 10.0.0.0/16
A subnet in that VPC with CIDR block 10.0.1.0/24
Instances running in that subnet with IP addresses 10.0.1.4 and 10.0.1.5
On-premises host networks using CIDR blocks 10.0.37.0/24 and 10.1.38.0/24
When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, the traffic is dropped because 10.0.37.0/24 is part of the larger prefix assigned to the VPC
(10.0.0.0/16). The instances can talk to hosts in the 10.1.38.0/24 space because that block isn't part of 10.0.0.0/16.
You can also create a VPC peering connection between your VPCs, or with a VPC in another AWS account. A VPC peering connection enables you to route traffic between the VPCs using
private IP addresses; however, you cannot create a VPC peering connection between VPCs that have overlapping CIDR blocks.
We therefore recommend that you create a VPC with a CIDR range large enough for expected future growth, but not one that overlaps with current or expected future subnets anywhere in
your corporate or home network, or that overlaps with current or future VPCs.
Question : Refer image and its description
A virtual private cloud (VPC) of size /16 (example CIDR: 10.0.0.0/16). This provides 65,536 private IP addresses.
A subnet of size /24 (example CIDR: 10.0.0.0/24). This provides 256 private IP addresses.
An instance with a private IP address in the subnet range (example: 10.0.0.6), and an Elastic IP address (example: 198.51.100.2)
Select correct statement
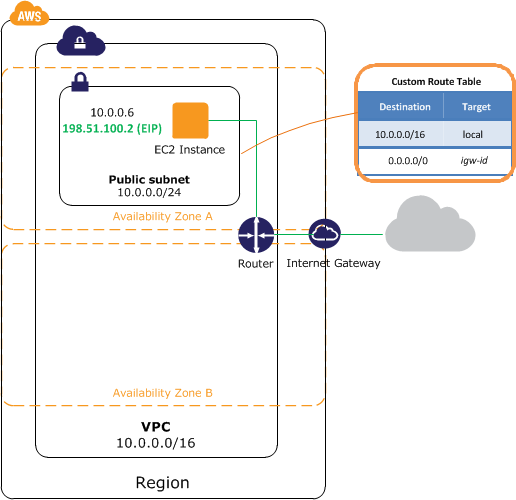
1. instance can communicate with other instances in the VPC
2. instance can be reached from the Internet
3. instance can not be reached from the Internet
4. 1 and 2
5. 1 and 3
Correct Answer : 4
Explanation: An instance with a private IP address in the subnet range (example: 10.0.0.6), which enables the instance to communicate with other instances in the VPC, and
an Elastic IP address (example: 198.51.100.2), which enables the instance to be reached from the Internet.
A route table entry that enables instances in the subnet to communicate with other instances in the VPC, and a route table entry that enables instances in the subnet to communicate
directly over the Internet.
Related Questions
Question : QuickTechie.com Inc is planning to setup a management network on the AWS VPC which is trying to secure the webserver on a single VPC instance such
that it allows the internet traffic as well as the back-end management traffic. QuickTechie admin wants to make sure that the back end management network interface
can receive the SSH traffic only from a selected IP range, while the internet facing webserver will have an IP address which can receive traffic from all the internet IPs.
How can the QuickTechie.com achieve this by running web server on a single instance?

1. The organization should create two network interfaces with the same subnet and security group to assign separate IPs to each network interface.
2. The organization should create two network interfaces with separate subnets so one instance can have two subnets and the respective security groups for controlled
access.
3. The organization should launch an instance with two separate subnets using the same network interface which allows to have a separate CIDR as well as security groups.
4. It is not possible to have two IP addresses for a single instance.
Question : HadoopExam.com has setup an application on AWS and wants to achieve scalability and HA for the application. Application should scale up and down
when there is a higher / reduced load on the application. Which of the below mentioned configurations is not required to be performed in this scenario?

1. Setup ELB with instances to distribute the load on the web server.
2. Setup schedule to shut off the instance when the instance is not in use.
3. Setup bootstrapping to start the web and DB servers on instance boot.
4. Create an AMI of a running instance and configure that AMI with AutoScaling.
Question : You can use Amazon Route health checking and DNS failover features to

1. enhance the availability of the applications running behind Elastic Load Balancers
2. run applications in multiple AWS regions and designate alternate load balancers for failover across regions
3. Both 1 and 2
4. None of above
Question : Using Elastic Load Balancing in your Amazon VPC, you can

1. balance load between tiers of your application within your VPC
2. specify whether the load balancer is internal to VPC.
3. specify whether the load balancer is internet-facing .
4. Only 1 and 2
5. 1,2 and 3
Question : You already know that the website you are going to re-launch on new servers will have millions of hits everyday. Hence, you need reserved instance
with known capacity for that you chose all upfront payment method. Now after launching the Reserved Instance you wish to change the aavailability zone. Which of '
the following is correct statement.

1. If you change the Availability Zone of an RI, its capacity reservation and pricing benefits no longer apply to the original
Availability Zone and start applying to usage in the new Availability Zone.
2. If you change the Availability Zone of an RI, its capacity reservation no longer apply to the original
Availability Zone and start applying to usage in the new Availability Zone.
3. If you change the Availability Zone of an RI, its capacity reservation and pricing benefits will apply to the original
Availability Zone as wel as in the new Availability Zone.
4. None of above
Question : You already know that the website you are going to re-launch on new servers will have millions of hits everyday. Hence, you need reserved instance
with known capacity for that you chose all upfront payment method.As you know you server is already running with lesser capacity, can you upgrade the same server
with RI ?

1. No, You can not
2. Yes, you can
3. It depend which AZ you are using
4. Yes, you can but you need to re-start the server after paying RI fee upfront.