AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
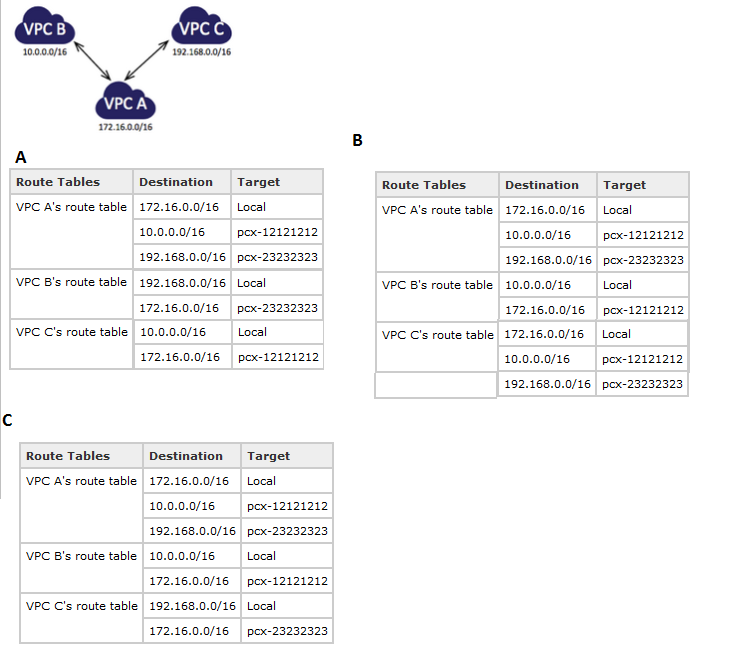
Question : You have a central VPC (VPC A), and you have a VPC peering connection
between VPC A and VPC B (pcx-12121212), and between VPC A and VPC C (pcx-23232323).
The VPCs are in the same AWS account, and do not have overlapping CIDR blocks.
You may want to use this 'flying V' configuration when you have resources on a
central VPC, such as a repository of services, that other VPCs need to access.
The other VPCs do not need access to each others' resources; they only
need access to resources on the central VPC.
VPC B and VPC C cannot send traffic directly to each other through VPC A.
VPC peering does not support transitive peering relationships, nor edge
to edge routing. You must create a VPC peering connection between
VPC B and VPC C in order to route traffic directly between them.
Select the correct route table for above scenerios.
1. A
2. B
3. C
4. A and B both
Correct Answer : 3
Explanation:
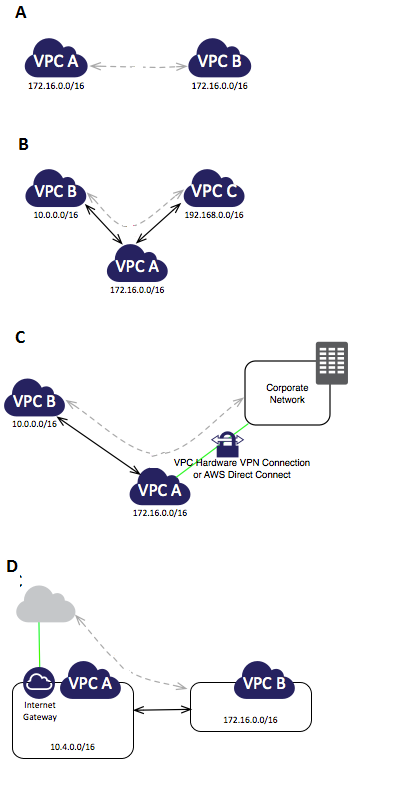
Question : Refer the image and identify which of the given VPC configuration is valid
1. A
2. B
3. C
4. D
5. None
Correct Answer : 5
Explanation:A- You cannot create a VPC peering connection between VPCs with matching or overlapping CIDR blocks.
B-You have a VPC peering connection between VPC A and VPC B (pcx-aaaabbbb), and between VPC A and VPC C (pcx-aaaacccc). There is no VPC peering connection between VPC B and VPC C.
You cannot route packets directly from VPC B to VPC C through VPC A.
To route packets directly between VPC B and VPC C, you can create a separate VPC peering connection between them (provided they do not have overlapping CIDR blocks).
C- You have a VPC peering connection between VPC A and VPC B (pcx-aaaabbbb). VPC A also has a VPN connection or an AWS Direct Connect connection to a corporate network. Edge to edge
routing is not supported; you cannot use VPC A to extend the peering relationship to exist between VPC B and the corporate network. For example, traffic from the corporate network
cant directly access VPC B by using the VPN connection or the AWS Direct Connect connection to VPC A.
D- You have a VPC peering connection between VPC A and VPC B (pcx-abababab). VPC A has an Internet gateway; VPC B does not. Edge to edge routing is not supported; you cannot use VPC
A to extend the peering relationship to exist between VPC B and the Internet. For example, traffic from the Internet cant directly access VPC B by using the Internet gateway
connection to VPC A.
Question : QuickTechie.com website is hosted in AWS and having the database and the app server on the AWS VPC. This is a MySQL database which you should be able
to upgrade or apply patches on the internet, however please not that no external request can be received from internet on this database. How will you set up this
configuration.

1. Setup MySQL DB in a private subnet with the security group allowing only outbound traffic.
2. Setup MySQL DB in a public subnet with the security group allowing only inbound data.
3. Setup MySQL DB in a local data center and use a private gateway to connect the application with DB.
4. Setup MySQL DB in a private subnet which is connected to the internet via NAT for outbound.
Correct Answer : 4
Explanation: By design, each subnet must be associated with a route table, which specifies the allowed routes for outbound traffic leaving the subnet. Every subnet that
you create is automatically associated with the main route table for the VPC. You can change the association, and you can change the contents of the main route table. For more
information, see Route Tables.
In the previous diagram, the route table associated with subnet 1 routes all traffic (0.0.0.0/0) to an Internet gateway (for example, igw-1a2b3c4d). Because instance V1 has an
Elastic IP address, it can be reached from the Internet.
Note
The Elastic IP address or public IP address that's associated with your instance is accessed through the Internet gateway of your VPC. Traffic that goes through a VPN connection
between your instance and another network traverses a virtual private gateway, not the Internet gateway, and therefore does not access the Elastic IP address or public IP address.
The instance V2 can't reach the Internet, but can reach other instances in the VPC. You can allow an instance in your VPC to initiate outbound connections to the Internet but prevent
unsolicited inbound connections from the Internet using a network address translation (NAT) instance. Because you can allocate a limited number of Elastic IP addresses, we recommend
that you use a NAT instance if you have more instances that require a static public IP address. For more information, see NAT Instances.
The route table associated with subnet 3 routes all traffic (0.0.0.0/0) to a virtual private gateway (for example, vgw-1a2b3c4d).
Related Questions
Question : Select the correct statement from below.
A. You can attach a network interface to an instance when it's running (hot attach), when it's stopped (warm attach), or when the instance is being launched (cold attach).
B. You can detach secondary (ethN) network interfaces when the instance is running or stopped. However, you can't detach the primary (eth0) interface.
C. You can attach a network interface in one subnet to an instance in another subnet in the same VPC, however, both the network interface and the instance must reside in the same
Availability Zone.
D. When launching an instance from the CLI or API, you can specify the network interfaces to attach to the instance for both the primary (eth0) and additional network interfaces.
E. Attaching another network interface to an instance is not a method to increase or double the network bandwidth to or from the dual-homed instance.

1. A,B,C
2. B,C,D,E
3. A,B,C,E
4. B,C,D
5. A,B,C,D,E
Question : An Elastic IP address (EIP) is a _________ IP address designed for ________ cloud computing.

1. dynamic, static
2. static, static
3. dynamic, dynamic
4. static, dynamic
Question : You have created an EC-Classic instance to host the webserver of QuickTechie.com blogging website. And you found that each instance in EC-Classic
has two IP addresses at launch: a private IP address and a public IP address that is mapped to the private IP address through network address translation (NAT).
The public IP address is allocated from the EC2-Classic public IP address pool, and is associated with __________________

1. your AWS account
2. your instance
3. your AWS account and instance
4. from common pool of IP addresses in AWS public cloud.
Question : Seledt the correct statement regarding key pair.
A. If you don't specify the name of an existing key pair when you launch an instance, you won't be able to connect to the instance.
B. Amazon EC2 doesn't keep a copy of your private key
C. If you lose the private key for an instance store-backed instance, you can't access the instance
D. If you lose the private key for an EBS-backed instance, you can't access the instance

1. A,B,C
2. B,C,D
3. A,C,D
4. A,B,C,D
Question : On the Key Pairs page in the Amazon EC console, the Fingerprint column displays the fingerprints generated from your key pairs.
If you created the key pair with a third-party tool and uploaded the public key to AWS
the fingerprint is calculated using __________

1. an MD5 hash function
2. an SHA-1 hash function
3. third party took key-pair are not supported bt AWS
4. Both 1 and 2 are used.
Question : You have launched and instance with the existing key pair. Now you have deleted this key pair from AWS. What would happen.

1. You have to terminate and delete this instance. As you will never be able to connect again.
2. As you still have private key with you, you can connect with the instance.
3. Once instance is launched with the key pair, it can never be deleted from AWS
4. None