AWS Certified SysOps Administrator - Associate Questions and Answers (Dumps and Practice Questions)
Question : You are designing a system that has a Bastion host. This component needs to be highly available without human intervention.
Which of the following approaches would you select?

1. Run the bastion on two instances one in each AZ
2. Run the bastion on an active Instance in one AZ and have an AMI ready to boot up in the event of failure
3. Access Mostly Uused Products by 50000+ Subscribers
4. Configure an ELB in front of the bastion instance
Correct Answer : Get Lastest Questions and Answer :
Explanation:1 is wrong because bastion is generally one host, 2 isn't HA without human intervention, and 4 is the same as 1, you don't usually want 2 of them running.
It will only launch another instance if your current instance dies. It means if the bastion host is in AZ-A and AZ-A goes offline, auto scaling will re-launch bastion host in AZ-B.
This means there will always be one bastion host running in a working AZ (unless both AZ's are offline at the same time, but AZ's are designed to not do this).
Question : Which of the following statements about this S bucket policy is true?
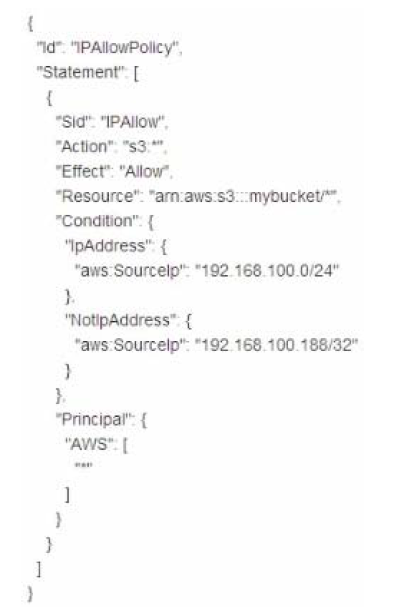
1. Denies the server with the IP address 192.168.100.0 full access to the "mybucket" bucket
2. Denies the server with the IP address 192.168.100.188 full access to the "mybucket" bucket
3. Access Mostly Uused Products by 50000+ Subscribers
4. Grants all the servers within the 192.168.100.188/32 subnet full access to the "mybucket" bucket
Correct Answer : Get Lastest Questions and Answer :
Question : Which of the following requires a custom CloudWatch metric to monitor?

1. Data transfer of an EC2 instance
2. Disk usage activity of an EC2 instance
3. Access Mostly Uused Products by 50000+ Subscribers
4. CPU Utilization of an EC2 instance
Correct Answer : Get Lastest Questions and Answer :
Explanation: However, there's one big missing feature in CloudWatch: it doesn't monitor your instance memory utilization. I suppose Amazon has all sorts of technical reasons not to provide
this very important metric out of the box (probably related to the fact that their monitoring is done from outside the instance VM), but really if you need to monitor servers, in
addition to CPU load and IO, memory utilization is one of the most important metrics to be aware of.
So, with a little bit of research I've found some scripts that utilize the CloudWatch API to send memory utilization info as a custom metric to AWS. However, most of these scripts
require that you provide some kind of credentials (API keys) and I feel really uncomfortable storing and managing API keys on all sorts of different machines, even with automation
tools like Chef. The less I have to do it, the better. Amazon has a pretty nice answer for that - IAM Roles which allow to authorize access to specific AWS services (including S3 and
CloudWatch) on an EC2 instance basis. Since we want all instances to be able to do certain things (like send their own metrics to CloudWatch or access our EC2 hosted private DEB
repo), all our EC2 servers get some permissions via IAM roles. But I couldn't find any solution that supports IAM roles and does the job right.
Related Questions
Question : A user is trying to understand the ACL and policy for an S bucket. Which of the below mentioned policy
permissions is equivalent to the WRITE ACL on a bucket?

1. s3:GetObjectAcl
2. s3:GetObjectVersion
3. Access Mostly Uused Products by 50000+ Subscribers
4. s3:DeleteObject
Question : A user has created an ELB with Auto Scaling. Which of the below mentioned offerings from ELB helps the user to stop sending new requests
traffic from the load balancer to the EC2 instance when the instance is being deregistered while continuing in-flight requests?

1. ELB sticky session
2. ELB deregistration check
3. Access Mostly Uused Products by 50000+ Subscribers
4. ELB auto registration Off
Ans : 3
Exp : The Elastic Load Balancer connection draining feature causes the load balancer to stop sending new requests to the back-end instances when the
instances are deregistering or become unhealthy, while ensuring that inflight requests continue to be served.
Question : A user has launched an EC instance from an instance store backed AMI. The infrastructure team wants to create an AMI from the running
instance. Which of the below mentioned steps will not be performed while creating the AMI?
1. Define the AMI launch permissions
2. Upload the bundled volume
3. Access Mostly Uused Products by 50000+ Subscribers
4. Bundle the volume
Ans : 1
Exp : When the user has launched an EC2 instance from an instance store backed AMI, it will need to follow certain steps, such as "Bundling the root
volume", "Uploading the bundled volume" and "Register the AMI". Once the AMI is created the user can setup the launch permission. However, it
is not required to setup during the launch.
Question : You are managing the AWS account of a big organization. The organization has more than + employees and they want to provide access to
the various services to most of the employees. Which of the below mentioned options is the best possible solution in this case?

1. The user should create a separate IAM user for each employee and provide access to them as per the policy
2. The user should create an IAM role and attach STS with the role. The user should attach that role to
the EC2 instance and setup AWS authentication on that server
3. Access Mostly Uused Products by 50000+ Subscribers
group for better access control
4. Attach an IAM role with the organization's authentication service to authorize each user for various
AWS services
Ans : 4
Exp : AWS Identity and Access Management is a web service which allows organizations to manage users and user permissions for various AWS
services. The user is managing an AWS account for an organization that already has an identity system, such as the login system for the
corporate network (SSO.. In this case, instead of creating individual IAM users or groups for each user who need AWS access, it may be more
practical to use a proxy server to translate the user identities from the organization network into the temporary AWS security credentials. This
proxy server will attach an IAM role to the user after authentication.
Question : A user has configured a VPC with a new subnet. The user has created a security group. The user wants to configure that instances of the same
subnet communicate with each other. How can the user configure this with the security group?

1. There is no need for a security group modification as all the instances can communicate with each
other inside the same subnet
2. Configure the subnet as the source in the security group and allow traffic on all the protocols and ports
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user has to use VPC peering to configure this
Ans : 3
Exp : A Virtual Private Cloud (VPC. is a virtual network dedicated to the user's AWS account. AWS provides two features that the user can use to
increase security in VPC: security groups and network ACLs. Security groups work at the instance level. If the user is using the default security
group it will have a rule which allows the instances to communicate with other. For a new security group the user has to specify the rule, add it to
define the source as the security group itself, and select all the protocols and ports for that source.
Question : A user is launching an instance. He is on the "Tag the instance" screen. Which of the below mentioned
information will not help the user understand the functionality of an AWS tag?

1. Each tag will have a key and value
2. The user can apply tags to the S3 bucket
3. Access Mostly Uused Products by 50000+ Subscribers
4. AWS tags are used to find the cost distribution of various resources
Ans : 3
Exp : AWS provides cost allocation tags to categorize and track the AWS costs. When the user applies tags to his AWS resources, AWS generates a
cost allocation report as a comma-separated value (CSV file. with the usage and costs aggregated by those tags. Each tag will have a key-value
and can be applied to services, such as EC2, S3, RDS, EMR, etc. The maximum size of a tag key is 128 unicode characters.
Question : A user has created a VPC with CIDR .../. The user has created public and VPN only subnets along with hardware VPN access to connect
to the user's datacenter. The user wants to make so that all traffic coming to the public subnet follows the organization's proxy policy. How can the
user make this happen?

1. Setting up a NAT with the proxy protocol and configure that the public subnet receives traffic from NAT
2. Settin up a proxy policy in the internet gateway connected with the public subnet
3. Access Mostly Uused Products by 50000+ Subscribers
4. Setting the route table and security group of the public subnet which receives traffic from a virtual private gateway
Ans : 4
Exp : The user can create subnets within a VPC. If the user wants to connect to VPC from his own data centre, he can setup public and VPN only
subnets which uses hardware VPN access to connect with his data centre. When the user has configured this setup, it will update the main route
table used with the VPN-only subnet, create a custom route table and associate it with the public subnet. It also creates an internet gateway for
the public subnet. By default the internet traffic of the VPN subnet is routed to a virtual private gateway while the internet traffic of the public subnet
is routed through the internet gateway. The user can set up the route and security group rules. These rules enable the traffic to come from the
organization's network over the virtual private gateway to the public subnet to allow proxy settings on that public subnet.
Question A user has created a VPC with CIDR .../. The user has created a public subnet with CIDR .../ and a private subnet with CIDR
20.0.0.128/25. The user has launched one instance each in the private and public subnets. Which of the below mentioned options cannot be the
correct IP address (private IP. assigned to an instance in the public or private subnet?

1. 20.0.0.255
2. 20.0.0.132
3. Access Mostly Uused Products by 50000+ Subscribers
4. 20.0.0.55
Question : A user has launched an EBS backed EC instance. The user has rebooted the instance. Which of the below mentioned statements is not true with
respect to the reboot action?

1. The private and public address remains the same
2. The Elastic IP remains associated with the instance
3. Access Mostly Uused Products by 50000+ Subscribers
4. The instance runs on a new host computer
Ans : 4
Exp : A user can reboot an EC2 instance using the AWS console, the Amazon EC2 CLI or the Amazon EC2 API. Rebooting an instance is equivalent to
rebooting an operating system. However, it is recommended that the user use the Amazon EC2 to reboot the instance instead of running the
operating system reboot command from the instance. The instance remains on the same host computer and maintains its public DNS name,
private IP address, and any data on its instance store volumes. It typically takes a few minutes for the reboot to complete, but the time it takes to
reboot depends on the instance configuration.
Question : A user has setup a web application on EC. The user is generating a log of the application performance at every second. There are multiple
entries for each second. If the user wants to send that data to CloudWatch every minute, what should he do?

1. The user should send only the data of the 60th second as CloudWatch will map the receive data
timezone with the sent data timezone
2. It is not possible to send the custom metric to CloudWatch every minute
3. Access Mostly Uused Products by 50000+ Subscribers
4. Calculate the average of one minute and send the data to CloudWatch
Ans : 3
Exp : Amazon CloudWatch aggregates statistics according to the period length that the user has specified while
getting data from CloudWatch. The user can publish as many data points as he wants with the same or similartime stamps. CloudWatch
aggregates them by the period length when the user calls get statistics about those data points. CloudWatch records the average (sum of all items
divided by the number of items. of the values received for every 1-minute period, as well as the number of samples, maximum value, and minimum
value for the same time period. CloudWatch will aggregate all the data which have time stamps within a one-minute period.
Question : An AWS root account owner is trying to create a policy to access RDS. Which of the below mentioned
statements is true with respect to the above information?

1. Create a policy which allows the users to access RDS and apply it to the RDS instances
2. The user cannot access the RDS database if he is not assigned the correct IAM policy
3. Access Mostly Uused Products by 50000+ Subscribers
4. The policy should be created for the user and provide access for RDS
Ans : 3
Exp : AWS Identity and Access Management is a web service which allows organizations to manage users and user permissions for various AWS
services. If the account owner wants to create a policy for RDS, the owner has to create an IAM user and define the policy which entitles the IAM
user with various RDS services such as Launch Instance, Manage security group, Manage parameter group etc.
Question : A user is using a small MySQL RDS DB. The user is experiencing high latency due to the Multi AZ feature.Which of the below mentioned options
may not help the user in this situation?

1. Schedule the automated back up in non-working hours
2. Use a large or higher size instance
3. Access Mostly Uused Products by 50000+ Subscribers
4. Take a snapshot from standby Replica
Question : An organization has configured the custom metric upload with CloudWatch. The organization has given permission to its employees to upload
data using CLI as well SDK. How can the user track the calls made to CloudWatch?

1. The user can enable logging with CloudWatch which logs all the activities
2. Use CloudTrail to monitor the API calls
3. Access Mostly Uused Products by 50000+ Subscribers
4. Enable detailed monitoring with CloudWatch
Ans : 2
Exp :AWS CloudTrail is a web service which will allow the user to monitor the calls made to the Amazon CloudWatch API for the organization's account,
including calls made by the AWS Management Console, Command Line Interface (CLI., and other services. When CloudTrail logging is turned on,
CloudWatch will write log files into the Amazon S3 bucket, which is specified during the CloudTrail configuration.
Question : A user has created a queue named "myqueue" with SQS. There are four messages published to queue which are not received by the consumer
yet. If the user tries to delete the queue, what will happen?

1. A user can never delete a queue manually. AWS deletes it after 30 days of inactivity on queue
2. It will delete the queue
3. Access Mostly Uused Products by 50000+ Subscribers
4. I t will ask user to delete the messages first
Ans : 2
Exp : SQS allows the user to move data between distributed components of applications so they can perform different tasks without losing messages or
requiring each component to be always available. The user can delete a queue at any time, whether it is empty or not. It is important to note that
queues retain messages for a set period of time. By default, a queue retains messages for four days.
Question : A user has launched a large EBS backed EC instance in the US-East-a region. The user wants to achieve Disaster Recovery (DR. for that
instance by creating another small instance in Europe.
How can the user achieve DR?
1. Copy the running instance using the "Instance Copy" command to the EU region
2. Create an AMI of the instance and copy the AMI to the EU region. Then launch the instance from the EU AMI
3. Access Mostly Uused Products by 50000+ Subscribers
4. Use the "Launch more like this" option to copy the instance from one region to another
Ans : 2
Exp :
To launch an EC2 instance it is required to have an AMI in that region. If the AMI is not available in that region, then create a new AMI or use the
copy command to copy the AMI from one region to the other region.
Question : A user has created numerous EBS volumes. What is the general limit for each AWS account for the maximum number of EBS volumes that can
be created?

1. 10000
2. 5000
3. Access Mostly Uused Products by 50000+ Subscribers
4. 1000
Ans : 2
Exp : A user can attach multiple EBS volumes to the same instance within the limits specified by his AWS account. Each AWS account has a limit on
the number of Amazon EBS volumes that the user can create, and the total storage available. The default limit for the maximum number of
volumes that can be created is 5000.
Question : A user has created a VPC with CIDR .../ using the wizard. The user has created a public subnet CIDR (.../. and VPN only
subnets CIDR (20.0.1.0/24. along with the VPN gateway (vgw-12345. to connect to the user's data centre. Which of the below mentioned options
is a valid entry for the main route table in this scenario?

1. Destination: 20.0.0.0/24 and Target: vgw-12345
2. Destination: 20.0.0.0/16 and Target: ALL
3. Access Mostly Uused Products by 50000+ Subscribers
4. Destination: 0.0.0.0/0 and Target: vgw-12345
Ans : 4
Exp : The user can create subnets as per the requirement within a VPC. If the user wants to connect VPC from his own data centre, he can setup a
public and VPN only subnet which uses hardware VPN access to connect with his data centre. When the user has configured this setup with
Wizard, it will create a virtual private gateway to route all traffic of the VPN subnet. Here are the valid entries for the main route table in this
scenario: Destination: 0.0.0.0/0 & Target: vgw-12345 (To route all internet traffic to the VPN gateway.
Destination: 20.0.0.0/16 & Target: local (To allow local routing in VPC.
Question :
What happens to an attached Elastic IP Address when the instance is stopped?

1. It stays attached to the instance.
2. It becomes unattached until the instance is restarted.
3. Access Mostly Uused Products by 50000+ Subscribers
4. It is disassociated from the account.
Question :
Your Database engine needs to build indexes. You configure a read replica from the current production system
and start the index building on the read replicas. What do you need to do once the indexes are complete?

1. Change the DNS to the read replica
2. Request AWS to change endpoint to read replica
3. Access Mostly Uused Products by 50000+ Subscribers
4. None of the above
Question :
Which storage engine is required for MySQL read replicas?

1. InnoDB
2. MyISAM
3. Access Mostly Uused Products by 50000+ Subscribers
4. Federated