AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : QuickTechie.com Inc has three different AWS acount for Admin, Billing and Technical Team, all are in three different regions. The Technical Team
created a file sharing site where all the technology employees data is uploaded. The Admin team uploads data about the all employee attendance to their DB
hosted in the VPC. The billing team needs to access data from the technology team to know the employees to calculate the salary based on the attendance.
How QuickTechie can set up this configuration in AWS?

1. Setup VPC peering for the VPCs of Admin and Billing.
2. Setup VPC peering for the VPCs of Admin and Tehnology Team
3. Setup VPC peering for the VPCs of Billing and technology Team as well as between the VPCs of Billing and Admin.
4. It is not possible to configure VPC peering since each department in separate regions.
Correct Answer : 4
Explanation: To create a VPC peering connection with another VPC, you need to be aware of the following limitations and rules:
You cannot create a VPC peering connection between VPCs that have matching or overlapping CIDR blocks.
You cannot create a VPC peering connection between VPCs in different regions.
You have a limit on the number active and pending VPC peering connections that you can have per VPC. For more information about VPC limits, see Amazon VPC Limits in the Amazon
VPC User Guide.
VPC peering does not support transitive peering relationships; in a VPC peering connection, your VPC will not have access to any other VPCs that the peer VPC may be peered with.
This includes VPC peering connections that are established entirely within your own AWS account. For more information about unsupported peering relationships, see Invalid VPC
Peering Connection Configurations. For examples of supported peering relationships, see VPC Peering Scenarios.
You cannot have more than one VPC peering connection between the same two VPCs at the same time.
The Maximum Transmission Unit (MTU) across a VPC peering connection is 1500 bytes.
A placement group can span peered VPCs; however, you will not get full-bisection bandwidth between instances in peered VPCs. For more information about placement groups, see
Placement Groups in the Amazon EC2 User Guide for Linux Instances.
Unicast reverse path forwarding in VPC peering connections is not supported. For more information, see Routing for Response Traffic.
You cannot reference a security group from the peer VPC as a source or destination for ingress or egress rules in your security group. Instead, reference CIDR blocks of the peer
VPC as the source or destination of your security group's ingress or egress rules.
Private DNS values cannot be resolved between instances in peered VPCs.
Question : In QuickTechie.com Inc, you have two departments Admin and HR both have AWS accounts. You work as a technical member with Admin department.
HR department has their own VPC and similarly Admin. Now as a admin you wish to make VPC peering with HR VPC.
To enable the flow of traffic between the peer VPCs (Admin and HR) using private IP addresses, you have to

1. add a route to one or more of your (Admin) VPC's route tables that points to the IP address range of the peer VPC
2. The owner of the peer VPC (HR) adds a route to one of their VPC's route tables that points to the IP address range of your VPC
3. Both 1 and 2
4. For Peering the VPC's private IP addresses are not supported.
Correct Answer : 3
Explanation: To establish a VPC peering connection, the owner of the requester VPC (or local VPC) sends a request to the owner of the peer VPC to create the VPC peering
connection. The peer VPC can be owned by you, or another AWS account. The owner of the peer VPC has to accept the VPC peering connection request to activate the VPC peering
connection. To enable the flow of traffic between the peer VPCs using private IP addresses, add a route to one or more of your VPC's route tables that points to the IP address range
of the peer VPC. The owner of the peer VPC adds a route to one of their VPC's route tables that points to the IP address range of your VPC.
Question : You have a VPC peering connection (pcx-) between VPC A and VPC B,
which are in the same AWS account, and do not have overlapping CIDR blocks.
You set up VPC A for your
accounting records, and VPC B for your financial records, and now you want each VPC to
be able to access each others' resources without restriction.
Select the correct route tables for each VPC point to the relevant VPC peering
connection to access the entire CIDR block of the peer VPC.
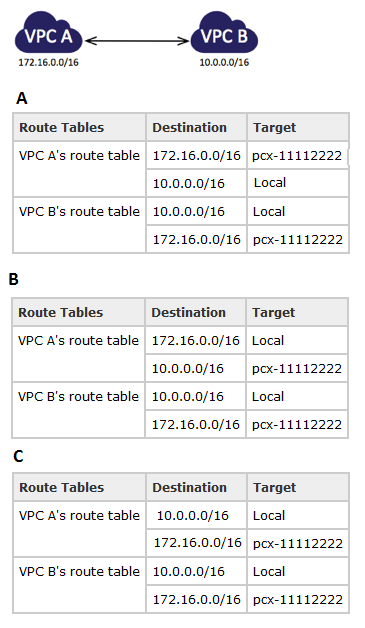
1. A
2. B
3. C
4. A,B
5. B,C
Correct Answer : 2
Explanation:
Related Questions
Question : An ENI is a virtual network interface that can include the whihc of the following attributes
A. a primary private IP address
B. one or more secondary private IP addresses
C. one Elastic IP address per private IP address
D. one public IP address, which can be auto-assigned to the network interface for eth0 when you launch an instance, but only when you create a network interface for eth0 instead
of using an existing network interface
E. one or more security groups
F. a MAC address
G. a source/destination check flag

1. A,B,C,D
2. C,D,E,F,G
3. A,B,C,D,E
4. A,B,C,D,E,F,G
Question : QuickTechie INc is planning to setup their blogging website on the AWS VPC and it shoud have automated HA and DR along with security.
Which of the below mentioned configurations satisfies the QuickTechie's requirement?

1. Create two separate VPCs and run RDS. RDS will have the multi AZ feature enabled which spans across these two VPCs using VPC peering. Setup the App server with one of
the public subnets of any VPC.
2. Create two separate VPCs in different zones. Setup two EC2 instances by installing a DB in the two different VPCs and enable the failover mechanism. Setup the App
server with one of the public subnets of any VPC.
3. Create a VPC with one private and one public subnet in separate AZs. Setup the EC2 instance with a DB in the private subnet and the web application in a public subnet.
4. Create a VPC with two private subnets and a public subnet. In separate AZs and setup RDS with the multi AZ feature by creating a subnet group. Launch a web application
in the public subnet.
Question : AcmeShell Inc is purchasing licensed software and license can be registered only to a specific MAC Address. Acmeshell Inc is going to host the
software in the AWS environment. How can the organization fulfil the license requirement as the MAC address changes every time an instance is started/stopped/terminated?

1. It is not possible to have a fixed MAC address with AWS.
2. The organization should use VPC with the private subnet and configure the MAC address with that subnet.
3. The organization should use VPC with an elastic network interface which will have a fixed MAC Address.
4. The organization should use VPC since VPC allows to configure the MAC address for each EC2 instance.
Question : In this scenario, the secondary network interface
on the instance handles __________ and the primary network interface
handles _________ traffic and is connected
to a separate subnet in your VPC that
has more restrictive access controls.
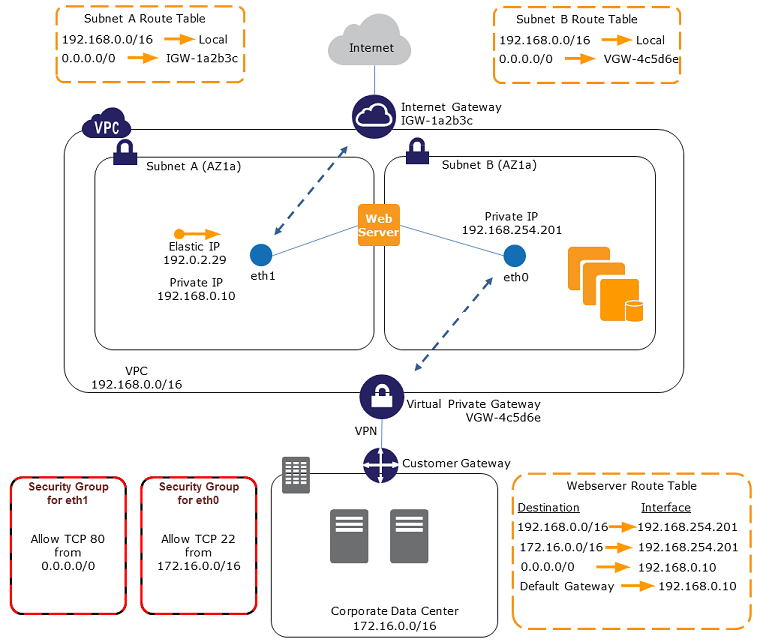
1. public-facing traffic, back-end management
2. back-end management, public-facing traffic
3. public-facing traffic, public-facing traffic
4. back-end management, back-end management
Question : Because of low budget constraint, you can not create full flash HA for the data base instances. However, you still need HA for your database instance,
and you are find with the little connectivity issue while failure. Which is the suitable solution for this problm.

1. If one of your instances serving a particular function fails, its elastic ip address can be attached to a replacement
or hot standby instance pre-configured for the same role in order to rapidly recover the service
2. If one of your instances serving a particular function fails, its private ip address can be attached to a replacement
or hot standby instance pre-configured for the same role in order to rapidly recover the service
3. If one of your instances serving a particular function fails, its network interface can be attached to a replacement
or hot standby instance pre-configured for the same role in order to rapidly recover the service
4. 1 and 2
5. 2 and 3
Question : Please map the following for Configuring Network Interfaces
a. hot attach
b. warm attach
c. cold attach
1. when instance running
2. when instance stopped
3. when the instance is being launched

1. a-1, b-2, c-3
2. a-2, b-1, c-3
3. a-2, b-3, c-1
4. a-3, b-2, c-3