AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : When you launch a DB instance inside any VPC (including a default VPC), you can designate whether the DB instance you create has a DNS that resolves
to a public IP address by using the Publicly Accessible parameter. This parameter lets you designate whether there is public access to the DB instance,
even if the VPC has a public IP address. If you want a DB instance in a VPC to be publicly accessible

1. you must also enable the VPC attributes DNS hostnames
2. you must also enable the VPC attributes DNS resolution
3. security group assigned to the DB instance should also permit
4. 1 and 3
5. 1 ,2 and 3
that is not publicly accessible. For example, you could create a VPC that has a public subnet and a private subnet. Amazon EC2 instances that function as web servers could be
deployed in the public subnet, and the Amazon RDS DB instances would be deployed in the private subnet. In such a deployment, only the web servers have access to the DB instances.
When you launch a DB instance inside any VPC (including a default VPC), you can designate whether the DB instance you create has a DNS that resolves to a public IP address by using
the PubliclyAccessible parameter. This parameter lets you designate whether there is public access to the DB instance, even if the VPC has a public IP address. Note that access to
the DB instance is ultimately controlled by the security group it uses, and that public access is not permitted if the security group assigned to the DB instance does not permit it.
If you want a DB instance in a VPC to be publicly accessible, you must also enable the VPC attributes DNS hostnames and DNS resolution.
Question : Previously created Oracle DB Instance in AWS was not in the VPC. Which of the following you have to do, so can launch your DB instance in VPC
1. create a VPC
2. create subnets in the VPC
3. create a DB subnet group that contains the subnets you created
4. create a VPC security group
5. must create a DB snapshot of your DB instance, and then restore that DB snapshot

1. 1,3,5
2. 2,4,5
3. 1,2,4,5
4. 1,2,3,4,5
Correct Answer : 4
Explanation: If you are moving a DB instance that is not in a VPC into a VPC, there are several steps you need to take. For example, if you want to move your DB instance that is not in a
VPC from a db.t1 DB instance class to a db.t2 DB instance class (which requires a VPC), you need to follow these steps. You must first create a VPC, create subnets in the VPC, create
a DB subnet group that contains the subnets you created, and then create a VPC security group so you can access the DB instance in the VPC. Finally, you must create a DB snapshot of
your DB instance, and then restore that DB snapshot using the VPC, DB subnet group, and VPC security group you created.
Question : Refer the image where the EC-Classic Instance is outside of the VPC,
now you wish to communicate with RDS (Which is inside VPC).
Which is the best solution for this
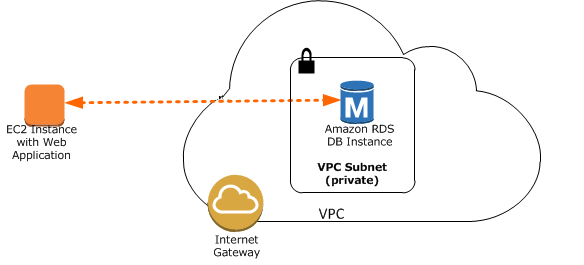
1. VPN
2. Remote Desktop
3. ClassicLink
4. AWS VPN CloudHub
Correct Answer : 3
Explanation: You can communicate between an EC2 instance that is not in an Amazon Virtual Private Cloud (VPC) and an Amazon RDS DB instance that is in a VPC by using
ClassicLink. Using this AWS feature, you can connect an EC2 instance to a logically isolated database where you define the IP address range and control the access control lists
(ACLs) to manage network traffic. You don't have to use public IP addresses or tunneling to communicate with the DB instance in the VPC. This arrangement provides you with higher
throughput and lower latency connectivity for inter-instance communications.
Note
The DB instance must be in a private subnet that is not open to the public (i.e. it cannot be set to publicly accessible).
Question : QuickTechie.com Inc has three different AWS acount for Admin, Billing and Technical Team. The Technical Team created a file sharing site where all the
technology employees data is uploaded. The Admin team uploads data about the all employee attendance to their DB hosted in the VPC. The billing team needs to access
data from the technology team to know the employees to calculate the salary based on the attendance. How QuickTechie can set up this configuration in AWS?

1. Setup VPC peering for the VPCs of Admin and Billing.
2. Setup VPC peering for the VPCs of Admin and Tehnology Team
3. Setup VPC peering for the VPCs of Billing and technology Team as well as between the VPCs of Billing and Admin.
4. It is not possible to configure VPC peering since each department has a separate AWS account.
Correct Answer : 3
Explanation: Amazon Virtual Private Cloud (Amazon VPC) enables you to launch Amazon Web Services (AWS) resources into a virtual network that you've defined. This virtual network closely
resembles a traditional network that you'd operate in your own data center, with the benefits of using the scalable infrastructure of AWS.
This guide is for customers who wish to set up VPC peering connections between VPCs in their own account, or with a VPC in another AWS account.
A VPC peering connection allows you to route traffic between the peer VPCs using private IP addresses; as if they are part of the same network.
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IP addresses. Instances in either VPC can
communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account within a
single region.
AWS uses the existing infrastructure of a VPC to create a VPC peering connection; it is neither a gateway nor a VPN connection, and does not rely on a separate piece of physical
hardware. There is no single point of failure for communication or a bandwidth bottleneck.
Related Questions
Question : When you are trying to delete default security group, what would happen in AWS VPC

1. Successfully deleted
2. It will be delted, but immediately another default one would be created without any rule.
3. you'll get the following error: Client.CannotDelete: the specified group: "sg-51530134" name: "default" cannot be deleted by a user.
4. Successfully deleted, with warning.
Question : AWS VPC automatically comes with a modifiable default network ACL, select the correct statement for this default ACL.

1. it allows all inbound and outbound traffic.
2. it allows all inbound traffic only.
3. it allows all outbound traffic only.
4. it would not allow all inbound and outbound traffic.
Question : Consider the following policy definition.
{
"Version": "2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action":["ec2:DescribeVpcs",
"ec2:DescribeSubnets",
"ec2:DescribeInternetGateways",
"ec2:DescribeCustomerGateways",
"ec2:DescribeVpnGateways",
"ec2:DescribeVpnConnections",
"ec2:DescribeRouteTables",
"ec2:DescribeAddresses",
"ec2:DescribeSecurityGroups",
"ec2:DescribeNetworkAcls",
"ec2:DescribeDhcpOptions",
"ec2:DescribeTags",
"ec2:DescribeInstances"],
"Resource":"*"
}
]
}
Select the correct statement which applies.

1. policy grants users permission to list your VPCs and their components. They can create, update, or delete them.
2. policy grants users permission to list your VPCs and their components. They can't create, update, or delete them.
3. policy grants users permission to list your VPCs and their components. They can create, update, but cant delete them.
4. grants users permission to launch instances, stop instances, start instances, terminate instances, and describe the available resources for Amazon EC2 and Amazon VPC.
Question : Consider the following policy definition.
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": "ec2:RunInstances",
"Resource": [
"arn:aws:ec2:region::image/ami-*",
"arn:aws:ec2:region:account:instance/*",
"arn:aws:ec2:region:account:subnet/subnet-1a2b3c4d",
"arn:aws:ec2:region:account:network-interface/*",
"arn:aws:ec2:region:account:volume/*",
"arn:aws:ec2:region:account:key-pair/*",
"arn:aws:ec2:region:account:security-group/sg-123abc123"
]
}
]
}
Select the correct statement which applies.

1. grants users permission to launch instances into a specific subnet, and to use a specific security group in the request
2. policy grants users permission to list your VPCs and their components. They can't create, update, or delete them.
3. policy grants users permission to list your VPCs and their components. They can create, update, but cant delete them.
4. grants users permission to launch instances, stop instances, start instances, terminate instances, and describe the available resources for Amazon EC2 and Amazon VPC.
Question : Question : Consider the following policy definition.
{
"Version": "2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action": "ec2:AcceptVpcPeeringConnection",
"Resource": "arn:aws:ec2:region:account:vpc-peering-connection/*",
"Condition": {
"ArnEquals": {
"ec2:RequesterVpc": "arn:aws:ec2:region:444455556666:vpc/*"
}
}
},
{
"Effect": "Allow",
"Action": "ec2:AcceptVpcPeeringConnection",
"Resource": "arn:aws:ec2:region:account:vpc/*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/Purpose": "Peering"
}
}
}
]
}
Select the correct statement which applies.

1. allows users to accept VPC peering connection requests from AWS account 444455556666 only
2. policy also grants users permissions to accept VPC peering requests only when your VPC has the tag Purpose=Peering.
3. policy grants users permission to list your VPCs and their components. They can create, update, but cant delete them.
4. 1 and 2
5. 2 and 3
Question : Select incorrect statement regarding elastic ip address in AWS VPC.

1. An Elastic IP address is a static, public IP address designed for dynamic cloud computing.
2. You can associate an Elastic IP address with any instance or network interface for your VPC.
3. With an Elastic IP address, you can mask the failure of an instance by rapidly remapping the address to another instance in your VPC.
4. advantage of associating the Elastic IP address with the network interface instead of directly with the instance is that you can move all the attributes of the network
interface from one instance to another in a single step.
5. None of above