AWS Certified SysOps Administrator - Associate Questions and Answers (Dumps and Practice Questions)
Question :
What would you need to edit to allow connections from your remove IP to your database instance?

1. VPC Network
2. Options Group
3. Access Mostly Uused Products by 50000+ Subscribers
4. Security Group
Correct Answer : Get Lastest Questions and Answer :
Explanation: DB Security Groups vs. VPC Security Groups
The following table shows the key differences between DB security groups and VPC security groups.
DB Security Group
Controls access to DB instances outside a VPC
Uses Amazon RDS APIs or Amazon RDS page of the AWS Management Console to create and manage group or rules
When you add a rule to a group, you do not need to specify port number or protocol.
Groups allow access from EC2 security groups in your AWS account or other accounts.
Security Group Scenario
VPC Security Group
Controls access to DB instances in VPC.
Uses Amazon EC2 APIs or Amazon VPC page of the AWS Management Console to create and manage group or rules.
When you add a rule to a group, you should specify the protocol as TCP, and specify the same port number that you used to create the DB instances (or Options) you plan to add as
members to the group.
Groups allow access from other VPC security groups in your VPC only.
A common use of an RDS instance in a VPC is to share data with an application server running in an EC2 instance in the same VPC and that is accessed by a client application outside
the VPC. For this scenario, you would do the following to create the necessary instances and security groups. You can use the RDS and VPC pages on the AWS Console or the RDS and EC2 APIs.
Create a VPC security group (for example, "sg-appsrv1") and define inbound rules that use as source the IP addresses of the client application. This security group allows your client
application to connect to EC2 instances in a VPC that uses this security group.
Create an EC2 instance for the application and add the EC2 instance to the VPC security group ("sg-appsrv1") you created in the previous step. The EC2 instance in the VPC shares the VPC security group with the DB instance.
Create a second VPC security group (for example, "sg-dbsrv1") and create a new rule by specifying the VPC security group you created in step 1 ("sg-appsrv1") as the source.
Create a new DB instance and add the DB instance to the VPC security group ("sg-dbsrv1") you created in the previous step. When you create the instance, use the same port number as
the one specified for the VPC security group ("sg-dbsrv1") rule you created in step 3.
Question :
RDS allows you to restore a database engine to a "point in time" (InnoDB for MySQL).

1. True
2. False
Correct Answer : Get Lastest Questions and Answer :
Explanation: The PointIn Time Restore and Snapshot Restore features of Amazon RDS for MySQL require a crash recoverable storage engine and are supported for InnoDB storage engine only.
While MySQL supports multiple storage engines with varying capabilities, not all of them are optimized for crash recovery and data durability. For example, MyISAM storage engine does
not support reliable crash recovery and may result in lost or corrupt data when MySQL is restarted after a crash, preventing Point In Time Restore or Snapshot restore from working as intended.
Read Replicas require a transactional storage engine and are only supported for the InnoDB storage engine.
Non transactional engines such as MyISAM might prevent Read Replicas from working as intended. However, if you still choose to use MyISAM with Read Replicas, we advise you to watch
the Amazon CloudWatch Replica Lag metric (available via the AWS Management Console or Amazon CloudWatch APIs) carefully and recreate the Read Replica should it fall behind due to
replication errors. The same considerations apply to the use of temporary tables and any other non transactional engines.

Correct Answer : Get Lastest Questions and Answer :
Explanation:
Question : In the Amazon Elastic Compute Cloud (Amazon EC) console
you have setup the Alarm as given setting, what would it implies
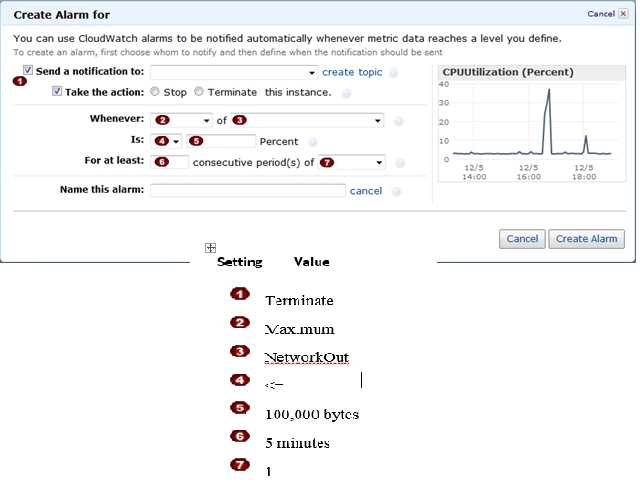
1. Create an alarm that terminates an instance that runs BigData MapReduce when it is no longer sending results data.
2. Create an alarm that stop an instance that runs BigData MapReduce when it is no longer sending results data.
3. Access Mostly Uused Products by 50000+ Subscribers
Correct Answer : Get Lastest Questions and Answer :
Explanation:
Related Questions
Question : A user has configured ELB with Auto Scaling. The user suspended the Auto Scaling terminate process only for a while. What will happen to the
availability zone rebalancing process AZRebalance. during this period?

1. Auto Scaling will not launch or terminate any instances
2. Auto Scaling will allow the instances to grow more than the maximum size
3. Access Mostly Uused Products by 50000+ Subscribers
4. It is not possible to suspend the terminate process while keeping the launch active
Question : A user has created a mobile application which makes calls to DynamoDB to fetch certain data. The application is using the DynamoDB SDK and
root account access/secret access key to connect to DynamoDB from mobile. Which of the below mentioned statements is true with respect to the
best practice for security in this scenario?

1. The user should create a separate IAM user for each mobile application and provide DynamoDB access with it
2. The user should create an IAM role with DynamoDB and EC2 access. Attach the role with EC2 and route all calls from the mobile through EC2
3. Access Mostly Uused Products by 50000+ Subscribers
4. Create an IAM Role with DynamoDB access and attach it with the mobile application
Question : A user is configuring the Multi AZ feature of an RDS DB. The user came to know that this RDS DB does not use the AWS technology, but uses
server mirroring to achieve HA. Which DB is the user using right now?

1. My SQL
2. Oracle
3. Access Mostly Uused Products by 50000+ Subscribers
4. PostgreSQL
Question : A user is receiving a notification from the RDS DB whenever there is a change in the DB security group. The user does not want to receive these
notifications for only a month. Thus, he does not want to delete the notification. How can the user configure this?

1. Change the Disable button for notification to "Yes" in the RDS console
2. Set the send mail flag to false in the DB event notification console
3. Access Mostly Uused Products by 50000+ Subscribers
4. Change the Enable button for notification to "No" in the RDS console
Question : A user has created a VPC with CIDR .../. The user has created one subnet with CIDR .../ by mistake. The user is trying to create
another subnet of CIDR 20.0.0.1/24. How can the user create the second subnet?

1. There is no need to update the subnet as VPC automatically adjusts the CIDR of the first subnet based on the second subnet's CIDR
2. The user can modify the first subnet CIDR from the console
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user can modify the first subnet CIDR with AWS CLI
Question : A user has created a VPC with the public and private subnets using the VPC wizard. The VPC has CIDR
20.0.0.0/16. The public subnet uses CIDR 20.0.1.0/24. The user is planning to host a web server in the public subnet port 80. and a DB server in
the private subnet port 3306.. The user is configuring a security group for the public subnet WebSecGrp. and the private subnet DBSecGrp..
Which of the below mentioned entries is required in the web server security group WebSecGrp.?

1. Configure Destination as DB Security group ID DbSecGrp. for port 3306 Outbound
2. 80 for Destination 0.0.0.0/0 Outbound
3. Access Mostly Uused Products by 50000+ Subscribers
4. Configure port 80 InBound for source 20.0.0.0/16