AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : QuickTechie.com is creating a VPC for their application hosting and has created two private subnets in the same AZ and created one subnet
in a separate zone. QuickTechie.com wants to make a HA system with the internal ELB. Which of the below mentioned statements is true with respect to an internal ELB in this scenario?

1. ELB can support only one subnet in each availability zone.
2. ELB does not allow subnet selection; instead it will automatically select all the available subnets of the VPC.
3. Access Mostly Uused Products by 50000+ Subscribers
4. If the user is creating an internal ELB, he should use only private subnets.
Correct Answer : Get Lastest Questions and Answer :
Exp: You can make your load balancer internal (private) or Internet-facing (public) when creating it within a VPC. When you make your load balancer internal, a DNS name will be
created, and it will contain the private IP address of the load balancer. Internal load balancer is not exposed to the internet. When you make your load balancer Internet-facing, a
DNS name will be created with the public IP address. The DNS records are publicly resolvable in both cases. For information on using both internal and Internet-facing load balancer
to support multiple tier architecture, see Internet-facing and Internal Load Balancers.
This topic uses an example to walk you through the process for creating a basic internal load balancer within your VPC and registering your EC2 instances with the newly created
internal load balancer. This example uses default configurations for security group, listener protocols and ports, and for the health check. When you create your internal load
balancer, you can optionally assign tags for your load balancer. Tags help you to categorize your load balancers in different ways, for example, by purpose, owner, or environment. If
you have not yet created your VPC environment for using an internal load balancer, create one before you proceed further. For information about creating a VPC environment, see
Configure a VPC for Elastic Load Balancing.
The following task list gives you a general overview of what you'll need to create a basic internal load balancer in a VPC. Then you'll step through detailed procedures for each part
of the creation process. Creating a Basic Internal Load Balancer in VPC
1. Configure the listeners for your load balancer by specifying the ports and protocols to use for front-end connection (client to load balancer) and back-end connection (load
balancer to back-end instance).
2. Configure a health check for your Amazon EC2 back-end instances.
3. Access Mostly Uused Products by 50000+ Subscribers
4. Select security groups to assign to your load balancer.
5. Add Amazon EC2 instances to your load balancer.
6. [optional] Add tags to your load balancer.
7. Review settings.
8. Create your load balancer.The Amazon Virtual Private Cloud (Amazon VPC) allows the user to define a virtual networking environment in a private, isolated section of the Amazon Web
Services (AWS) cloud. The user has complete control over the virtual networking environment. Within this virtual private cloud, the user can launch AWS resources, such as an ELB, and
EC2 instances.
There are two ELBs available with VPC: internet facing and internal (private) ELB. For internal servers, such as App servers the organization can create an internal load balancer in
their VPC and then place back-end application instances behind the internal load balancer. The internal load balancer will route requests to the back-end application instances, which
are also using private IP addresses and only accept requests from the internal load balancer.
The Internal ELB supports only one subnet in each AZ and asks the user for selecting subnet while configuring internal ELB.
Question : HadoopExam.com has setup a VPC with public and private subnets and does not want everyone to connect to the private VPC instance.
Instead it wants to setup secure access from a single IP. Which of the below mentioned options fits best as a solution?

1. Create an IAM user who will have secure access to the private subnet.
2. Allow only the public subnet to SSH to the private subnet.
3. Access Mostly Uused Products by 50000+ Subscribers
4. Create a NAT instance which allows access only from the selected IP address.
Correct Answer : Get Lastest Questions and Answer :
Exp: SSH and bastion servers
By default, Linux instances in EC2 use SSH key files for authentication instead of SSH usernames and passwords. Using key files can reduce the chance of somebody trying to guess the
password to gain access to the instance. But using key pairs with a bastion host can present a challenge-connecting to instances in the private subnets requires a private key, but
you should never store private keys on the bastion.
One solution is to use SSH agent forwarding (ssh-agent) on the client. This allows an administrator to connect from the bastion to another instance without storing the private key on
the bastion. That's the approach I'll discuss in this post.
Configuring ssh-agent
The first step in using SSH agent forwarding with EC2 instances is to configure a bastion in your VPC. We suggest that the instance you use for your bastion be purpose-built and that
you use it only as a bastion and not for anything else. The bastion should also be set up with a security group that's configured to listen only on the SSH port (TCP/22). For
additional security, you can harden the instance further. It's beyond the scope of this post to discuss hardening in detail, but doing so involves tasks like enabling SELinux, using
a remote syslog server for logs, and configuring host-based intrusion detection. For more in-depth information, see OS Hardening Principles on the etutorials.org site. A Virtual
Private Cloud (VPC) is a virtual network dedicated to the user's AWS account. It enables the user to launch AWS resources into a virtual network that the user has defined. It is
recommended that for a private subnet the organization should setup a bastion host machine which will be able to SSH to a private subnet.
By default, Linux instances in EC2 use the SSH key files for authentication instead of the SSH usernames and passwords. Using key files can reduce the chance of somebody trying to
guess the password to gain access to the instance. However, using key pairs with a bastion host can present a challenge wherein connecting to instances in the private subnets
requires a private key.
Thus, the user should never store private keys on the bastion host. For this purpose it is recommended to setup the SSH forwarding agent (ssh-agent) on the bastion host. This allows
an administrator to connect from the bastion to another instance without storing the private key on the bastion.
Always remember the following when configuring your bastion:
Never place your SSH private keys on the bastion instance. Instead, use SSH agent forwarding to connect first to the bastion and from there to other instances in private subnets.
This lets you keep your SSH private key just on your computer.
Configure the security group on the bastion to allow SSH connections (TCP/22) only from known and trusted IP addresses.
Always have more than one bastion. You should have a bastion in each availability zone (AZ) where your instances are. If your deployment takes advantage of a VPC VPN, also have a
bastion on premises.
Configure Linux instances in your VPC to accept SSH connections only from bastion instances.
Question : QuickTechie.com is planning to setup a 'warm standby' to AWS for fast recovery of the application in case of DR.
Which of the below mentioned configurations will not fit the 'warm standby' requirement setup?

1. Setup EC2 with the smallest server and ELB which run continuously.
2. Setup the backup data on S3 and transfer data regularly to S3 using the storage gateway.
3. Access Mostly Uused Products by 50000+ Subscribers
4. Mirror the data from in premise data to EC2.
Correct Answer : Get Lastest Questions and Answer :
Exp: AWS has many solutions for DR and HA. When the organization wants to have HA and DR with a warm standby they need to setup the environment in AWS and keeps it running
continuously to recover the data. The organization should setup and replicate the data regularly to EC2 with minimal sizes. The AMIs should also be maintained in the AWS environment.
When required for recovery, this AWS standby environment can be scaled up for the production load. In this recovery phase, the organization can change the DNS to route traffic to AWS
as well as use AutoScaling to manage a higher load. If the organization keeps copying data to S3 it will take a much longer time to recovery and may not fit the warm standby
solution.
Related Questions
Question : You have a central VPC (VPC A), and you have a VPC peering connection
between VPC A and VPC B (pcx-12121212), and between VPC A and VPC C (pcx-23232323).
The VPCs are in the same AWS account, and do not have overlapping CIDR blocks.
You may want to use this 'flying V' configuration when you have resources on a
central VPC, such as a repository of services, that other VPCs need to access.
The other VPCs do not need access to each others' resources; they only
need access to resources on the central VPC.
VPC B and VPC C cannot send traffic directly to each other through VPC A.
VPC peering does not support transitive peering relationships, nor edge
to edge routing. You must create a VPC peering connection between
VPC B and VPC C in order to route traffic directly between them.
Select the correct route table for above scenerios.
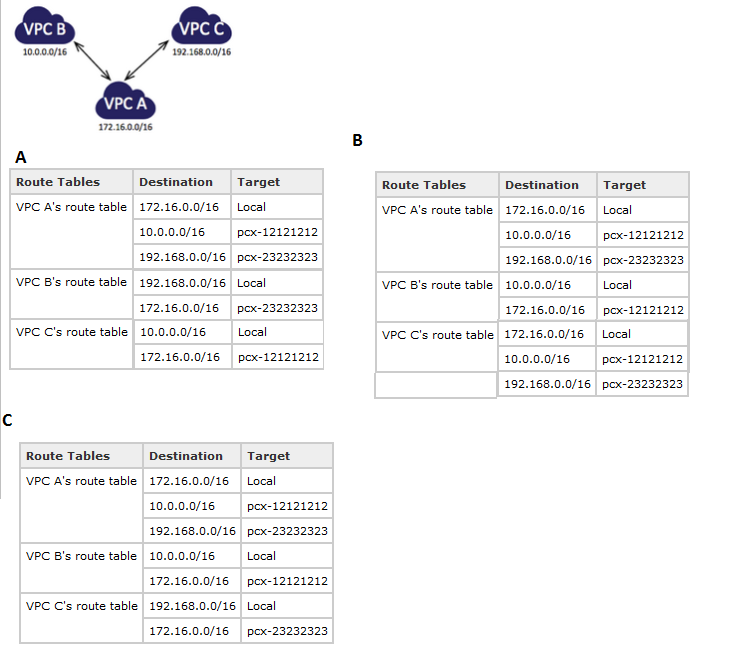
1. A
2. B
3. C
4. A and B both
Question : Refer the image and identify which of the given VPC configuration is valid
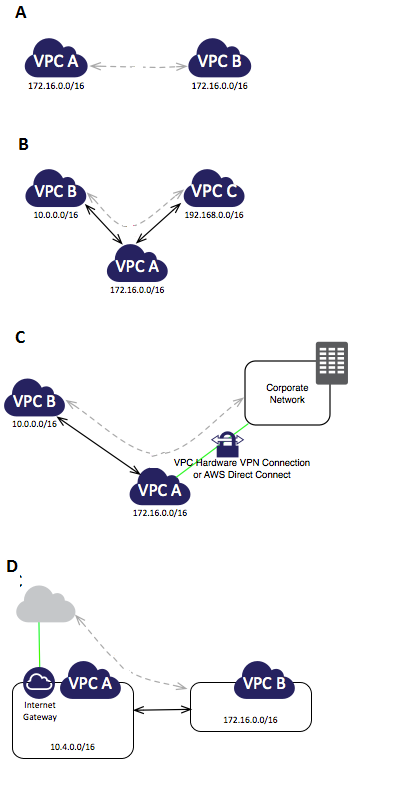
1. A
2. B
3. C
4. D
5. None
Question : QuickTechie.com website is hosted in AWS and having the database and the app server on the AWS VPC. This is a MySQL database which you should be able
to upgrade or apply patches on the internet, however please not that no external request can be received from internet on this database. How will you set up this
configuration.

1. Setup MySQL DB in a private subnet with the security group allowing only outbound traffic.
2. Setup MySQL DB in a public subnet with the security group allowing only inbound data.
3. Setup MySQL DB in a local data center and use a private gateway to connect the application with DB.
4. Setup MySQL DB in a private subnet which is connected to the internet via NAT for outbound.
Question : You have created a VPC with the IP addresses, now after months you found that, this VPC is not enough. You need the VPC with at least IP
addresses. So what you have to do upgrade the VPC with 32 IP addresses.

1. Change the CIDR block and add new 16 IP addresses.
2. Delete the CIDR block and add all 32 IP addresses again.
3. More than 16 IP addresses are not supported in VPC
4. Delete the VPC, and then create a new, larger VPC
Question : Consider the below scenerio.
A VPC with CIDR block 10.0.0.0/16
A subnet in that VPC with CIDR block 10.0.1.0/24
Instances running in that subnet with IP addresses 10.0.1.4 and 10.0.1.5
On-premises host networks using CIDR blocks 10.0.37.0/24 and 10.1.38.0/24
Select the correct statement from below.
1. When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, the traffic is dropped
2. When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, can talk
3. When those instances in the VPC try to talk to hosts in the 10.1.38.0/24 address space, the traffic is dropped
4. Only 1 and 3
5. Only 2 and 3
Question : Refer image and its description
A virtual private cloud (VPC) of size /16 (example CIDR: 10.0.0.0/16). This provides 65,536 private IP addresses.
A subnet of size /24 (example CIDR: 10.0.0.0/24). This provides 256 private IP addresses.
An instance with a private IP address in the subnet range (example: 10.0.0.6), and an Elastic IP address (example: 198.51.100.2)
Select correct statement
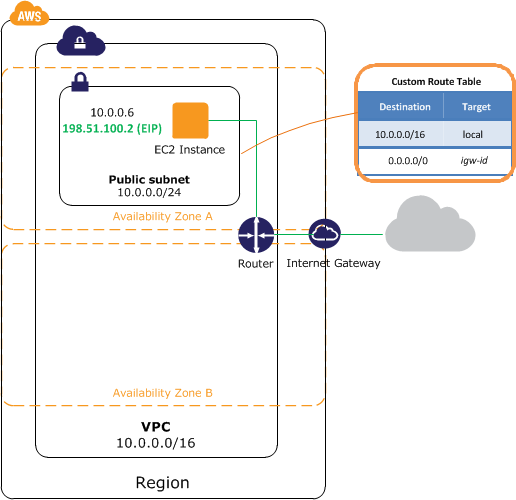
1. instance can communicate with other instances in the VPC
2. instance can be reached from the Internet
3. instance can not be reached from the Internet
4. 1 and 2
5. 1 and 3