AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : You have created a subnet and specified the CIDR block .../ for subnet. Please select the correct statement

1. It supports 24 IP addresses, You can break this CIDR block into two subnets, each supporting 12 IP addresses
2. It supports 128 IP addresses, You can break this CIDR block into two subnets, each supporting 64 IP addresses
3. It supports 256 IP addresses, You can break this CIDR block into two subnets, each supporting 128 IP addresses
4. It supports 24 IP addresses, You can not break this CIDR block into two subnets
Correct Answer : 3
Explanation: When you create a subnet, you specify the CIDR block for the subnet. The CIDR block of a subnet can be the same as the CIDR block for the VPC (for a single
subnet in the VPC), or a subset (to enable multiple subnets). The allowed block size is between a /28 netmask and /16 netmask. If you create more than one subnet in a VPC, the CIDR
blocks of the subnets must not overlap.
For example, if you create a VPC with CIDR block 10.0.0.0/24, it supports 256 IP addresses. You can break this CIDR block into two subnets, each supporting 128 IP addresses. One
subnet uses CIDR block 10.0.0.0/25 (for addresses 10.0.0.0 - 10.0.0.127) and the other uses CIDR block 10.0.0.128/25 (for addresses 10.0.0.128 - 10.0.0.255).
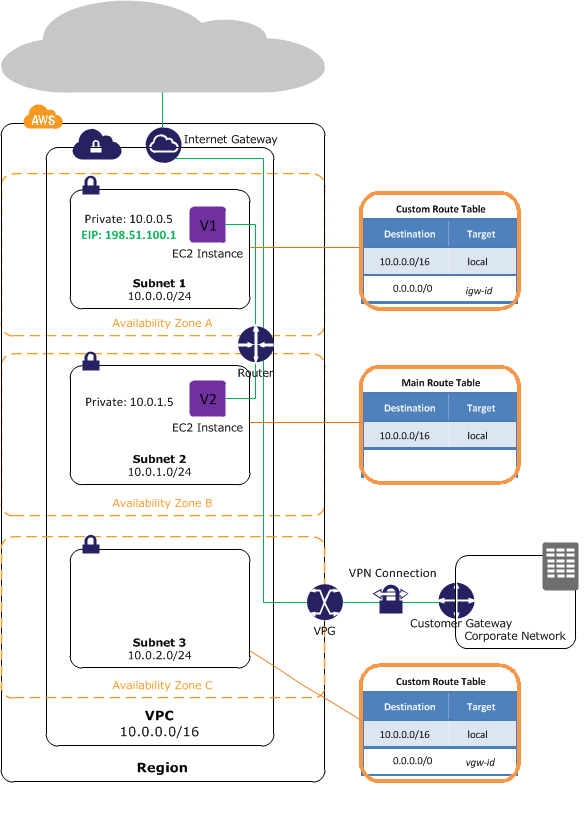
Question : In the given diagram,
the route table associated with subnet 1 routes
all traffic __________ to an Internet
gateway (for example, igw-1a2b3c4d).
Because instance V1 has an Elastic IP address,
it can be reached from the Internet.
1. (0.0.0.16/0)
2. (0.0.0.24/0)
3. (0.0.0.0/0)
4. (0.0.0.5/0)
Correct Answer : 3
Explanation: By design, each subnet must be associated with a route table, which specifies the allowed routes for outbound traffic leaving the subnet. Every subnet that you create is
automatically associated with the main route table for the VPC. You can change the association, and you can change the contents of the main route table. For more information, see
Route Tables. In the previous diagram, the route table associated with subnet 1 routes all traffic (0.0.0.0/0) to an Internet gateway (for example, igw-1a2b3c4d). Because instance V1
has an Elastic IP address, it can be reached from the Internet.
Note : The Elastic IP address or public IP address that's associated with your instance is accessed through the Internet gateway of your VPC. Traffic that goes through a VPN
connection between your instance and another network traverses a virtual private gateway, not the Internet gateway, and therefore does not access the Elastic IP address or public IP
address. The instance V2 can't reach the Internet, but can reach other instances in the VPC. You can allow an instance in your VPC to initiate outbound connections to the Internet
but prevent unsolicited inbound connections from the Internet using a network address translation (NAT) instance. Because you can allocate a limited number of Elastic IP addresses,
we recommend that you use a NAT instance if you have more instances that require a static public IP address. For more information, see NAT Instances. The route table associated with
subnet 3 routes all traffic (0.0.0.0/0) to a virtual private gateway (for example, vgw-1a2b3c4d).
Question : QuickTechie.com is planning to implement a scalable web application with AWS EC to achieve HA with multi AZ features. The application requires an
Weblogic J2EE app server and may require a load which will be catered by 2 large instances. Select the configurations is better choice for HA in DR

1. Launch only one large instance and setup Auto Scaling with ELB.
2. Launch two large instances in separate AZs and load balance them with ELB.
3. Launch 8 small EC2 instances with two instances in each zone for better HA and DR and load balance each with ELB.
4. Launch 4 small instances in separate AZs and load balance them with ELB.
Correct Answer : 4
Explanation: Amazon Web Services includes some features and offerings that enable effective compartmentalization. Firstly, many Amazon Web Services-for example, Amazon S3 and Amazon RDS-are
themselves internally compartmentalized and make use of active redundancy designs so that when failures occur they are hidden.
We also offer web services and resources in a range of sizes, along with automation in the form of auto-scaling, CloudFormation templates, and Opsworks recipes that make it easy to
manage a higher number of instances.
There is a subtle but important distinction between running a small number of large instances, and a large number of small instances. Four m3.xlarge instances cost as much as two
m3.2xlarge instances and provide the same amount of CPU and storage; but for high availability configurations, using four instances requires only a 33% failover capacity buffer and
any host-level problem may impact one quarter of your load, whereas using two instances means a 100% buffer and any problem may impact half of your load.
Thirdly, Amazon Web Services has pre-made compartments: up to four availability zones per region. These availability zones are deeply compartmentalized down to the datacenter,
network and power level. QuickTechie.com can always launch multiple EC2 instances in the same region across multiple AZs for HA and DR. It is recommended that the application should
be load balanced with ELB for better load distribution. When the organization requires two large instances for the app server it is recommended to distribute the load by creating
four small instances across AZs. The two large instances give only 50% redundancy while the four small instances give 75% redundancy. As cost wise both the scenarios are the same it
is recommended to run four small instances across AZs. Suppose that we create a web site or web service that utilizes four availability zones. This means we need a 25% failover
capacity buffer per zone (which compares well to a 100% failover capacity buffer in a standard two data center model). Our service consists of a front end, two dependent backend
services ("Foo" and "Bar") and a data-store (for this example, we'll use S3).
Related Questions
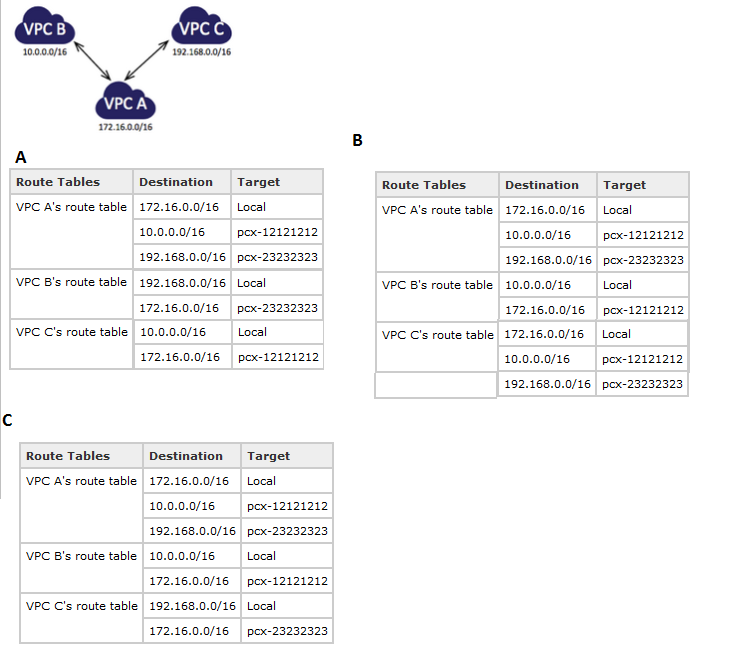
Question : You have a central VPC (VPC A), and you have a VPC peering connection
between VPC A and VPC B (pcx-12121212), and between VPC A and VPC C (pcx-23232323).
The VPCs are in the same AWS account, and do not have overlapping CIDR blocks.
You may want to use this 'flying V' configuration when you have resources on a
central VPC, such as a repository of services, that other VPCs need to access.
The other VPCs do not need access to each others' resources; they only
need access to resources on the central VPC.
VPC B and VPC C cannot send traffic directly to each other through VPC A.
VPC peering does not support transitive peering relationships, nor edge
to edge routing. You must create a VPC peering connection between
VPC B and VPC C in order to route traffic directly between them.
Select the correct route table for above scenerios.
1. A
2. B
3. C
4. A and B both
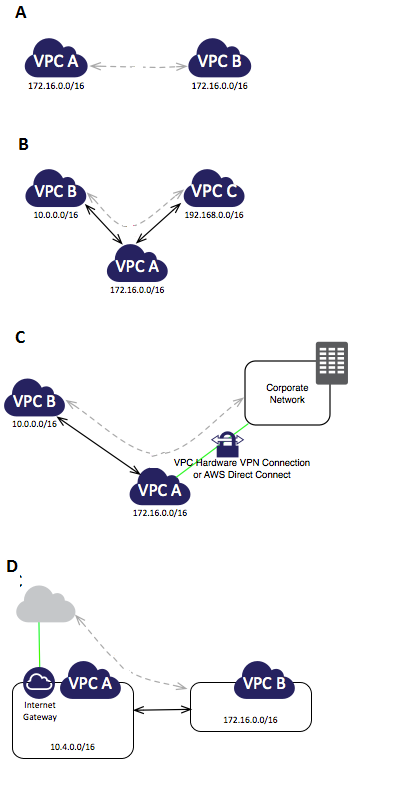
Question : Refer the image and identify which of the given VPC configuration is valid
1. A
2. B
3. C
4. D
5. None
Question : QuickTechie.com website is hosted in AWS and having the database and the app server on the AWS VPC. This is a MySQL database which you should be able
to upgrade or apply patches on the internet, however please not that no external request can be received from internet on this database. How will you set up this
configuration.

1. Setup MySQL DB in a private subnet with the security group allowing only outbound traffic.
2. Setup MySQL DB in a public subnet with the security group allowing only inbound data.
3. Setup MySQL DB in a local data center and use a private gateway to connect the application with DB.
4. Setup MySQL DB in a private subnet which is connected to the internet via NAT for outbound.
Question : You have created a VPC with the IP addresses, now after months you found that, this VPC is not enough. You need the VPC with at least IP
addresses. So what you have to do upgrade the VPC with 32 IP addresses.

1. Change the CIDR block and add new 16 IP addresses.
2. Delete the CIDR block and add all 32 IP addresses again.
3. More than 16 IP addresses are not supported in VPC
4. Delete the VPC, and then create a new, larger VPC
Question : Consider the below scenerio.
A VPC with CIDR block 10.0.0.0/16
A subnet in that VPC with CIDR block 10.0.1.0/24
Instances running in that subnet with IP addresses 10.0.1.4 and 10.0.1.5
On-premises host networks using CIDR blocks 10.0.37.0/24 and 10.1.38.0/24
Select the correct statement from below.
1. When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, the traffic is dropped
2. When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, can talk
3. When those instances in the VPC try to talk to hosts in the 10.1.38.0/24 address space, the traffic is dropped
4. Only 1 and 3
5. Only 2 and 3
Question : Refer image and its description
A virtual private cloud (VPC) of size /16 (example CIDR: 10.0.0.0/16). This provides 65,536 private IP addresses.
A subnet of size /24 (example CIDR: 10.0.0.0/24). This provides 256 private IP addresses.
An instance with a private IP address in the subnet range (example: 10.0.0.6), and an Elastic IP address (example: 198.51.100.2)
Select correct statement
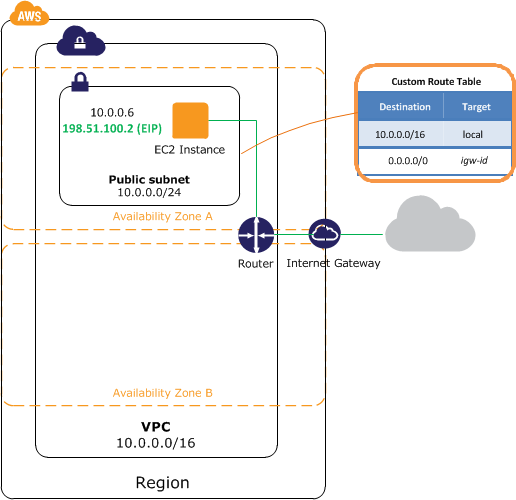
1. instance can communicate with other instances in the VPC
2. instance can be reached from the Internet
3. instance can not be reached from the Internet
4. 1 and 2
5. 1 and 3