AWS Certified SysOps Administrator - Associate Questions and Answers (Dumps and Practice Questions)
Question : A user has configured ELB with SSL using a security policy for secure negotiation between the client and load balancer. The ELB security policy
supports various ciphers. Which of the below mentioned options helps identify the matching cipher at the client side to the ELB cipher list when
client is requesting ELB DNS over SSL?

1. Cipher Protocol
2. Client Configuration Preference
3. Access Mostly Uused Products by 50000+ Subscribers
4. Load Balancer Preference
Correct Answer : Get Lastest Questions and Answer :
Explanation: Elastic Load Balancing uses a Secure Socket Layer SSL negotiation configuration which is known as a Security Policy.
It is used to negotiate the SSL connections between a client and the load balancer. When client is requesting ELB DNS over SSL
and if the load balancer is configured to support the Server Order Preference, then the load balancer gets to select the first
cipher in its list that matches any one of the ciphers in the client's list. Server Order Preference ensures that the
load balancer determines which cipher is used for the SSL connection.
Question : A user has created a VPC with public and private subnets. The VPC has CIDR .../. The private subnet uses CIDR .../ and the
public subnet uses CIDR 20.0.0.0/24. The user is planning to host a web server in the public subnet port 80. and a DB server in the private
subnet port 3306.. The user is configuring a security group of the NAT instance. Which of the below mentioned entries is not required for the NAT security group?

1. For Inbound allow Source: 20.0.1.0/24 on port 80
2. For Outbound allow Destination: 0.0.0.0/0 on port 80
3. Access Mostly Uused Products by 50000+ Subscribers
4. For Outbound allow Destination: 0.0.0.0/0 on port 443
Correct Answer : Get Lastest Questions and Answer :
A user can create a subnet with VPC and launch instances inside that subnet. If the user has created a public private subnet to host the web
server and DB server respectively, the user should configure that the instances in the private subnet can connect to the internet using the NAT
instances. The user should first configure that NAT can receive traffic on ports 80 and 443 from the private subnet. Thus, allow ports 80 and 443 in
Inbound for the private subnet 20.0.1.0/24. Now to route this traffic to the internet configure ports 80 and 443 in Outbound with destination
0.0.0.0/0. The NAT should not have an entry for the public subnet CIDR.
Question : A user has created an application which will be hosted on EC. The application makes calls to DynamoDB to fetch certain data. The application is
using the DynamoDB SDK to connect with from the EC2 instance. Which of the below mentioned statements is true with respect to the best
practice for security in this scenario?

1. The user should attach an IAM role with DynamoDB access to the EC2 instance
2. The user should create an IAM user with DynamoDB access and use its credentials within the application to connect with DynamoDB
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user should create an IAM user with DynamoDB and EC2 access. Attach the user with the application so that it does not use the root
account credentials
Correct Answer : Get Lastest Questions and Answer :
Explanation: With AWS IAM a user is creating an application which runs on an EC2 instance and makes requests to AWS, such as DynamoDB or S3 calls.
Here it is recommended that the user should not create an IAM user and pass the user's credentials to the application or embed those credentials
inside the application. Instead, the user should use roles for EC2 and give that role access to DynamoDB /S3. When the roles are attached to EC2,
it will give temporary security credentials to the application hosted on that EC2, to connect with DynamoDB / S3.
Related Questions
Question : Which services allow the customer to retain full administrative privileges of the underlying EC instances?
Choose 2 answers
A. Amazon Elastic Map Reduce
B. Elastic Load Balancing
C. AWS Elastic Beanstalk
D. Amazon Elasticache
E. Amazon Relational Database service

1. A,B
2. A,D
3. Access Mostly Uused Products by 50000+ Subscribers
4. C,D
5. A,C
Question : You have a web-style application with a stateless but CPU and memory-intensive web tier running on a cc xlarge EC instance inside of a VPC. The instance when under
load is having problems returning requests within the SLA as defined by your business. The application maintains its state in a DynamoDB table, but the data tier is properly
provisioned and responses are consistently fast. How can you best resolve the issue of the application responses not meeting your SLA?

1. Add another cc2 8xlarge application instance, and put both behind an Elastic Load Balancer
2. Move the cc2 8xlarge to the same Availability Zone as the DynamoDB table
3. Access Mostly Uused Products by 50000+ Subscribers
4. Move the database from DynamoDB to RDS MySQL in scale-out read-replica configuration
Question : You are managing a legacy application Inside VPC with hard coded IP addresses in its configuration.
Which two mechanisms will allow the application to failover to new instances without the need for reconfiguration? Choose 2 answers
A. Create an ELB to reroute traffic to a failover instance
B. Create a secondary ENI that can be moved to a failover instance
C. Use Route53 health checks to fail traffic over to a failover instance
D. Assign a secondary private IP address to the primary ENI that can be moved to a failover instance

1. A,B
2. B,C
3. Access Mostly Uused Products by 50000+ Subscribers
4. C,D
5. A,C
Question : You are designing a system that has a Bastion host. This component needs to be highly available without human intervention.
Which of the following approaches would you select?

1. Run the bastion on two instances one in each AZ
2. Run the bastion on an active Instance in one AZ and have an AMI ready to boot up in the event of failure
3. Access Mostly Uused Products by 50000+ Subscribers
4. Configure an ELB in front of the bastion instance
Question : Which of the following statements about this S bucket policy is true?
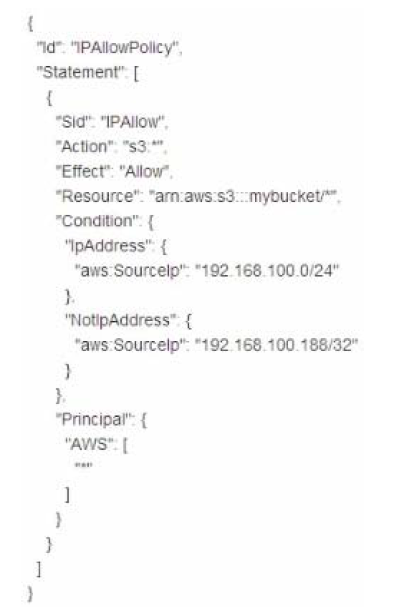
1. Denies the server with the IP address 192.168.100.0 full access to the "mybucket" bucket
2. Denies the server with the IP address 192.168.100.188 full access to the "mybucket" bucket
3. Access Mostly Uused Products by 50000+ Subscribers
4. Grants all the servers within the 192.168.100.188/32 subnet full access to the "mybucket" bucket
Question : Which of the following requires a custom CloudWatch metric to monitor?

1. Data transfer of an EC2 instance
2. Disk usage activity of an EC2 instance
3. Access Mostly Uused Products by 50000+ Subscribers
4. CPU Utilization of an EC2 instance