AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : QuickTechie.com has multiple branch offices and existing Internet connections. You also have multiple VPN connections with AWS, but wish to
establish secure communication between sites. Select the correct statement.

1. you can provide secure communication between sites using the AWS VPN CloudHub
2. To use the AWS VPN CloudHub, you must create a virtual private gateway with multiple customer gateways
3. To use the AWS VPN CloudHub, you must create a virtual private gateway with single customer gateways
4. 1 and 2
5. 1 and 3
Correct Answer : 4
Explanation: If you have multiple VPN connections, you can provide secure communication between sites using the AWS VPN CloudHub. The VPN CloudHub operates on a simple
hub-and-spoke model that you can use with or without a VPC. This design is suitable for customers with multiple branch offices and existing Internet connections who'd like to
implement a convenient, potentially low-cost hub-and-spoke model for primary or backup connectivity between these remote offices.
To use the AWS VPN CloudHub, you must create a virtual private gateway with multiple customer gateways, each with unique Border Gateway Protocol (BGP) Autonomous System Numbers
(ASNs). Customer gateways advertise the appropriate routes (BGP prefixes) over their VPN connections. These routing advertisements are received and re-advertised to each BGP peer,
enabling each site to send data to and receive data from the other sites. The routes for each spoke must have unique ASNs and the sites must not have overlapping IP ranges. Each
site can also send and receive data from the VPC as if they were using a standard VPN connection.
Sites that use AWS Direct Connect connections to the virtual private gateway can also be part of the AWS VPN CloudHub. For example, your corporate headquarters in New York can have
an AWS Direct Connect connection to the VPC and your branch offices can use VPN connections to the VPC. The branch offices in Los Angeles and Miami can send and receive data with
each other and with your corporate headquarters, all using the AWS VPN CloudHub.
To configure the AWS VPN CloudHub, you use the AWS Management Console to create multiple customer gateways, each with the unique public IP address of the gateway and a unique ASN.
Next, you create a VPN connection from each customer gateway to a common virtual private gateway. Each VPN connection must advertise its specific BGP routes. This is done using the
network statements in the VPN configuration files for the VPN connection. The network statements differ slightly depending on the type of router you use. When using an AWS VPN
CloudHub, you pay typical Amazon VPC VPN connection rates. You are billed the connection rate for each hour that each VPN is connected to the virtual private gateway. When you send
data from one site to another using the AWS VPN CloudHub, there is no cost to send data from your site to the virtual private gateway. You only pay standard AWS data transfer rates
for data that is relayed from the virtual private gateway to your endpoint. For example, if you have a site in Los Angeles and a second site in New York and both sites have a VPN
connection to the virtual private gateway, you pay $.05 per hour for each VPN connection (for a total of $.10 per hour). You also pay the standard AWS data transfer rates for all
data that you send from Los Angeles to New York (and vice versa) that traverses each VPN connection; network traffic sent over the VPN connection to the virtual private gateway is
free but network traffic sent over the VPN connection from the virtual private gateway to the endpoint is billed at the standard AWS data transfer rate.
Question : There is a big Investment bank who wish to use cloud infrastructire. However, they are having huge portfolio of customers and thier data needs to
be confidential. They are having 100 number of App Servers and In house Oracle database setup. How they can leverage the AWS cloud infra.

1. The organization should plan the all 100 app server on the public subnet and oracle rds in a private subnet so it will not be in the public cloud.
2. The organization should plan the app server on the public subnet and keep the Oracle database in the organization's data center and connect them with the VPN gateway.
3. The organization should plan the app server on the public subnet and use RDS with the private subnet for a secure data operation.
4. The organization should use the public subnet for the app server and use RDS with a storage gateway to access as well as sync the data securely from the local data center.
Correct Answer : 2
Explanation: A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS cloud. You
can launch your AWS resources, such as Amazon EC2 instances, into your VPC. When you create a VPC, you specify the set of IP addresses for the VPC in the form of a Classless
Inter-Domain Routing (CIDR) block (for example, 10.0.0.0/16).
You can optionally set up a connection between your VPC and your corporate or home network. If you have an IP address prefix in your VPC that overlaps with one of your networks'
prefixes, any traffic to the network's prefix is dropped. For example, let's say that you have the following:
A VPC with CIDR block 10.0.0.0/16
A subnet in that VPC with CIDR block 10.0.1.0/24
Instances running in that subnet with IP addresses 10.0.1.4 and 10.0.1.5
On-premises host networks using CIDR blocks 10.0.37.0/24 and 10.1.38.0/24
When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, the traffic is dropped because 10.0.37.0/24 is part of the larger prefix assigned to the VPC
(10.0.0.0/16). The instances can talk to hosts in the 10.1.38.0/24 space because that block isn't part of 10.0.0.0/16.
You can also create a VPC peering connection between your VPCs, or with a VPC in another AWS account. A VPC peering connection enables you to route traffic between the VPCs using
private IP addresses; however, you cannot create a VPC peering connection between VPCs that have overlapping CIDR blocks. For more information, see VPC Peering.
We therefore recommend that you create a VPC with a CIDR range large enough for expected future growth, but not one that overlaps with current or expected future subnets anywhere in
your corporate or home network, or that overlaps with current or future VPCs.
Question : Select the correct statement regrading VPC and Subnet

1. You can create a VPC that spans multiple Availability Zones
2. subnet must reside entirely within one Availability Zone and cannot span zones
3. If a subnet have a route to the Internet gateway, the subnet is known as a private subnet
4. 1,2
5. 1,2,3
Correct Answer : 4
Explanation: You can create a VPC that spans multiple Availability Zones. For more information, see Creating a VPC. After creating a VPC, you can add one or more subnets
in each Availability Zone. Each subnet must reside entirely within one Availability Zone and cannot span zones. Availability Zones are distinct locations that are engineered to be
isolated from failures in other Availability Zones. By launching instances in separate Availability Zones, you can protect your applications from the failure of a single location.
AWS assigns a unique ID to each subnet. You can optionally add an Internet gateway to enable communication over the Internet, or a virtual private network (VPN) connection to enable
communication with your network. If a subnet's traffic is routed to an Internet gateway, the subnet is known as a public subnet.
If a subnet doesn't have a route to the Internet gateway, the subnet is known as a private subnet. In this diagram, subnet 2 is a private subnet.
If a subnet doesn't have a route to the Internet gateway, but has its traffic routed to a virtual private gateway, the subnet is known as a VPN-only subnet.
Related Questions
Question : When you launch a DB instance inside any VPC (including a default VPC), you can designate whether the DB instance you create has a DNS that resolves
to a public IP address by using the Publicly Accessible parameter. This parameter lets you designate whether there is public access to the DB instance,
even if the VPC has a public IP address. If you want a DB instance in a VPC to be publicly accessible

1. you must also enable the VPC attributes DNS hostnames
2. you must also enable the VPC attributes DNS resolution
3. security group assigned to the DB instance should also permit
4. 1 and 3
5. 1 ,2 and 3
that is not publicly accessible. For example, you could create a VPC that has a public subnet and a private subnet. Amazon EC2 instances that function as web servers could be
deployed in the public subnet, and the Amazon RDS DB instances would be deployed in the private subnet. In such a deployment, only the web servers have access to the DB instances.
When you launch a DB instance inside any VPC (including a default VPC), you can designate whether the DB instance you create has a DNS that resolves to a public IP address by using
the PubliclyAccessible parameter. This parameter lets you designate whether there is public access to the DB instance, even if the VPC has a public IP address. Note that access to
the DB instance is ultimately controlled by the security group it uses, and that public access is not permitted if the security group assigned to the DB instance does not permit it.
If you want a DB instance in a VPC to be publicly accessible, you must also enable the VPC attributes DNS hostnames and DNS resolution.
Question : Previously created Oracle DB Instance in AWS was not in the VPC. Which of the following you have to do, so can launch your DB instance in VPC
1. create a VPC
2. create subnets in the VPC
3. create a DB subnet group that contains the subnets you created
4. create a VPC security group
5. must create a DB snapshot of your DB instance, and then restore that DB snapshot

1. 1,3,5
2. 2,4,5
3. 1,2,4,5
4. 1,2,3,4,5
Question : Refer the image where the EC-Classic Instance is outside of the VPC,
now you wish to communicate with RDS (Which is inside VPC).
Which is the best solution for this
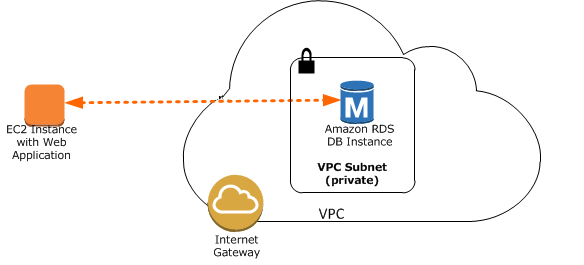
1. VPN
2. Remote Desktop
3. ClassicLink
4. AWS VPN CloudHub
Question : QuickTechie.com Inc has three different AWS acount for Admin, Billing and Technical Team. The Technical Team created a file sharing site where all the
technology employees data is uploaded. The Admin team uploads data about the all employee attendance to their DB hosted in the VPC. The billing team needs to access
data from the technology team to know the employees to calculate the salary based on the attendance. How QuickTechie can set up this configuration in AWS?

1. Setup VPC peering for the VPCs of Admin and Billing.
2. Setup VPC peering for the VPCs of Admin and Tehnology Team
3. Setup VPC peering for the VPCs of Billing and technology Team as well as between the VPCs of Billing and Admin.
4. It is not possible to configure VPC peering since each department has a separate AWS account.
Question : QuickTechie.com Inc has three different AWS acount for Admin, Billing and Technical Team, all are in three different regions. The Technical Team
created a file sharing site where all the technology employees data is uploaded. The Admin team uploads data about the all employee attendance to their DB
hosted in the VPC. The billing team needs to access data from the technology team to know the employees to calculate the salary based on the attendance.
How QuickTechie can set up this configuration in AWS?

1. Setup VPC peering for the VPCs of Admin and Billing.
2. Setup VPC peering for the VPCs of Admin and Tehnology Team
3. Setup VPC peering for the VPCs of Billing and technology Team as well as between the VPCs of Billing and Admin.
4. It is not possible to configure VPC peering since each department in separate regions.
Question : In QuickTechie.com Inc, you have two departments Admin and HR both have AWS accounts. You work as a technical member with Admin department.
HR department has their own VPC and similarly Admin. Now as a admin you wish to make VPC peering with HR VPC.
To enable the flow of traffic between the peer VPCs (Admin and HR) using private IP addresses, you have to

1. add a route to one or more of your (Admin) VPC's route tables that points to the IP address range of the peer VPC
2. The owner of the peer VPC (HR) adds a route to one of their VPC's route tables that points to the IP address range of your VPC
3. Both 1 and 2
4. For Peering the VPC's private IP addresses are not supported.
Question : You have a VPC peering connection (pcx-) between VPC A and VPC B,
which are in the same AWS account, and do not have overlapping CIDR blocks.
You set up VPC A for your
accounting records, and VPC B for your financial records, and now you want each VPC to
be able to access each others' resources without restriction.
Select the correct route tables for each VPC point to the relevant VPC peering
connection to access the entire CIDR block of the peer VPC.
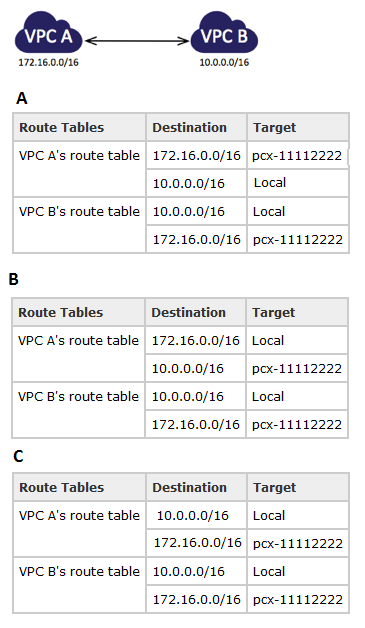
1. A
2. B
3. C
4. A,B
5. B,C