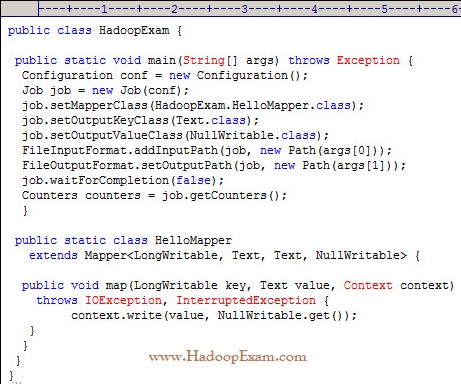
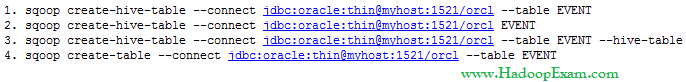
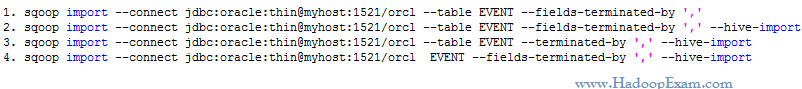
AWS Certified SysOps Administrator - Associate Questions and Answers (Dumps and Practice Questions)
Question : A user wants to find the particular error that occurred on a certain date in the AWS MySQL RDS DB. Which of the below mentioned activities may
help the user to get the data easily?

1. It is not possible to get the log files for MySQL RDS
2. Find all the transaction logs and query on those records
3. Access Mostly Uused Products by 50000+ Subscribers
4. Download the log file to DynamoDB and search for the record
Correct Answer : Get Lastest Questions and Answer :
Explanation: The user can view, download, and watch the database logs using the Amazon RDS console, the Command Line Interface CLI. or the Amazon
RDS API. For the MySQL RDS, the user can view the error log, slow query log, and general logs. The user can also view the MySQL logs easily
by directing the logs to a database table in the main database and querying that table.
Question : A user is trying to send custom metrics to CloudWatch using the PutMetricData APIs. Which of the below
mentioned points should the user needs to take care while sending the data to CloudWatch?

1. The size of a request is limited to 8KB for HTTP GET requests and 40KB for HTTP POST requests
2. The size of a request is limited to 128KB for HTTP GET requests and 64KB for HTTP POST requests
3. Access Mostly Uused Products by 50000+ Subscribers
4. The size of a request is limited to 16KB for HTTP GET requests and 80KB for HTTP POST requests
Correct Answer : Get Lastest Questions and Answer :
Explanation: With AWS CloudWatch, the user can publish data points for a metric that share not only the same time stamp, but also the same namespace and
dimensions. CloudWatch can accept multiple data points in the same PutMetricData call with the same time stamp. The only thing that the user
needs to take care of is that the size of a PutMetricData request is limited to 8KB for HTTP GET requests and 40KB for HTTP POST requests.
Question : An AWS account owner has setup multiple IAM users. One IAM user only has CloudWatch access. He has setup the alarm action which stops the
EC2 instances when the CPU utilization is below the threshold limit. What will happen in this case?

1. It is not possible to stop the instance using the CloudWatch alarm
2. CloudWatch will stop the instance when the action is executed
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user can setup the action but it will not be executed if the user does not have EC2 rights
Correct Answer : Get Lastest Questions and Answer :
Amazon CloudWatch alarms watch a single metric over a time period that the user specifies and performs one or more actions based on the value
of the metric relative to a given threshold over a number of time periods. The user can setup an action which stops the instances when their CPU
utilization is below a certain threshold for a certain period of time. The EC2 action can either terminate or stop the instance as part of the EC2
action. If the IAM user has read/write permissions for Amazon CloudWatch but not for Amazon EC2, he can still create an alarm. However, the
stop or terminate actions will not be performed on the Amazon EC2 instance.
Related Questions
Question : A user has setup an EBS backed instance and a CloudWatch alarm when the CPU utilization is more than %. The user has setup the alarm to
watch it for 5 periods of 5 minutes each. The CPU utilization is 60% between 9 AM to 6 PM. The user has stopped the EC2 instance for 15
minutes between 11 AM to 11:15 AM. What will be the status of the alarm at 11:30 AM?

1. Alarm
2. OK
3. Access Mostly Uused Products by 50000+ Subscribers
4. Error
Question A user is running one instance for only hours every day. The user wants to save some cost with the instance. Which of the below mentioned
Reserved Instance categories is advised in this case?
1. The user should not use RI; instead only go with the on-demand pricing
2. The user should use the AWS high utilized RI
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user should use the AWS low utilized RI
Ans : 1
Exp : The AWS Reserved Instance provides the user with an option to save some money by paying a one-time fixed amount and then save on the
hourly rate. It is advisable that if the user is having 30% or more usage of an instance per day, he should go for a RI. If the user is going to use an
EC2 instance for more than 2200-2500 hours per year, RI will help the user save some cost. Here, the instance is not going to run for less than
1500 hours. Thus, it is advisable that the user should use the on-demand pricing.
Question : A user has setup an RDS DB with Oracle. The user wants to get notifications when someone modifies the
security group of that DB. How can the user configure that?
1. It is not possible to get the notifications on a change in the security group
2. Configure SNS to monitor security group changes
3. Access Mostly Uused Products by 50000+ Subscribers
4. Configure the CloudWatch alarm on the DB for a change in the security group
Ans : 3
Exp : Amazon RDS uses the Amazon Simple Notification Service to provide a notification when an Amazon RDS event occurs. These events can be
configured for source categories, such as DB instance, DB security group, DB snapshot and DB parameter group. If the user is subscribed to a
Configuration Change category for a DB security group, he will be notified when the DB security group is changed.
Question : A user is trying to setup a recurring Auto Scaling process. The user has setup one process to scale up every day at am and scale down at PM.
The user is trying to setup another recurring process which scales up on the 1st of every month at 8 AM and scales down the same day at 7 PM.
What will Auto Scaling do in this scenario?

1. Auto Scaling will execute both processes but will add just one instance on the 1st
2. Auto Scaling will add two instances on the 1st of the month
3. Access Mostly Uused Products by 50000+ Subscribers
4. Auto Scaling will throw an error since there is a conflict in the schedule of two separate Auto Scaling
Question : A user is planning to setup infrastructure on AWS for the Christmas sales. The user is planning to use Auto Scaling based on the schedule for
proactive scaling. What advise would you give to the user?

1. It is good to schedule now because if the user forgets later on it will not scale up
2. The scaling should be setup only one week before Christmas
3. Access Mostly Uused Products by 50000+ Subscribers
4. It is not advisable to use scheduled based scaling
Question : A user is trying to understand the ACL and policy for an S bucket. Which of the below mentioned policy
permissions is equivalent to the WRITE ACL on a bucket?

1. s3:GetObjectAcl
2. s3:GetObjectVersion
3. Access Mostly Uused Products by 50000+ Subscribers
4. s3:DeleteObject
Question : A user has created an ELB with Auto Scaling. Which of the below mentioned offerings from ELB helps the user to stop sending new requests
traffic from the load balancer to the EC2 instance when the instance is being deregistered while continuing in-flight requests?

1. ELB sticky session
2. ELB deregistration check
3. Access Mostly Uused Products by 50000+ Subscribers
4. ELB auto registration Off
Ans : 3
Exp : The Elastic Load Balancer connection draining feature causes the load balancer to stop sending new requests to the back-end instances when the
instances are deregistering or become unhealthy, while ensuring that inflight requests continue to be served.
Question : A user has launched an EC instance from an instance store backed AMI. The infrastructure team wants to create an AMI from the running
instance. Which of the below mentioned steps will not be performed while creating the AMI?
1. Define the AMI launch permissions
2. Upload the bundled volume
3. Access Mostly Uused Products by 50000+ Subscribers
4. Bundle the volume
Ans : 1
Exp : When the user has launched an EC2 instance from an instance store backed AMI, it will need to follow certain steps, such as "Bundling the root
volume", "Uploading the bundled volume" and "Register the AMI". Once the AMI is created the user can setup the launch permission. However, it
is not required to setup during the launch.
Question : You are managing the AWS account of a big organization. The organization has more than + employees and they want to provide access to
the various services to most of the employees. Which of the below mentioned options is the best possible solution in this case?

1. The user should create a separate IAM user for each employee and provide access to them as per the policy
2. The user should create an IAM role and attach STS with the role. The user should attach that role to
the EC2 instance and setup AWS authentication on that server
3. Access Mostly Uused Products by 50000+ Subscribers
group for better access control
4. Attach an IAM role with the organization's authentication service to authorize each user for various
AWS services
Ans : 4
Exp : AWS Identity and Access Management is a web service which allows organizations to manage users and user permissions for various AWS
services. The user is managing an AWS account for an organization that already has an identity system, such as the login system for the
corporate network (SSO.. In this case, instead of creating individual IAM users or groups for each user who need AWS access, it may be more
practical to use a proxy server to translate the user identities from the organization network into the temporary AWS security credentials. This
proxy server will attach an IAM role to the user after authentication.
Question : A user has configured a VPC with a new subnet. The user has created a security group. The user wants to configure that instances of the same
subnet communicate with each other. How can the user configure this with the security group?

1. There is no need for a security group modification as all the instances can communicate with each
other inside the same subnet
2. Configure the subnet as the source in the security group and allow traffic on all the protocols and ports
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user has to use VPC peering to configure this
Ans : 3
Exp : A Virtual Private Cloud (VPC. is a virtual network dedicated to the user's AWS account. AWS provides two features that the user can use to
increase security in VPC: security groups and network ACLs. Security groups work at the instance level. If the user is using the default security
group it will have a rule which allows the instances to communicate with other. For a new security group the user has to specify the rule, add it to
define the source as the security group itself, and select all the protocols and ports for that source.
Question : A user is launching an instance. He is on the "Tag the instance" screen. Which of the below mentioned
information will not help the user understand the functionality of an AWS tag?

1. Each tag will have a key and value
2. The user can apply tags to the S3 bucket
3. Access Mostly Uused Products by 50000+ Subscribers
4. AWS tags are used to find the cost distribution of various resources
Ans : 3
Exp : AWS provides cost allocation tags to categorize and track the AWS costs. When the user applies tags to his AWS resources, AWS generates a
cost allocation report as a comma-separated value (CSV file. with the usage and costs aggregated by those tags. Each tag will have a key-value
and can be applied to services, such as EC2, S3, RDS, EMR, etc. The maximum size of a tag key is 128 unicode characters.
Question : A user has created a VPC with CIDR .../. The user has created public and VPN only subnets along with hardware VPN access to connect
to the user's datacenter. The user wants to make so that all traffic coming to the public subnet follows the organization's proxy policy. How can the
user make this happen?

1. Setting up a NAT with the proxy protocol and configure that the public subnet receives traffic from NAT
2. Settin up a proxy policy in the internet gateway connected with the public subnet
3. Access Mostly Uused Products by 50000+ Subscribers
4. Setting the route table and security group of the public subnet which receives traffic from a virtual private gateway
Ans : 4
Exp : The user can create subnets within a VPC. If the user wants to connect to VPC from his own data centre, he can setup public and VPN only
subnets which uses hardware VPN access to connect with his data centre. When the user has configured this setup, it will update the main route
table used with the VPN-only subnet, create a custom route table and associate it with the public subnet. It also creates an internet gateway for
the public subnet. By default the internet traffic of the VPN subnet is routed to a virtual private gateway while the internet traffic of the public subnet
is routed through the internet gateway. The user can set up the route and security group rules. These rules enable the traffic to come from the
organization's network over the virtual private gateway to the public subnet to allow proxy settings on that public subnet.
Question A user has created a VPC with CIDR .../. The user has created a public subnet with CIDR .../ and a private subnet with CIDR
20.0.0.128/25. The user has launched one instance each in the private and public subnets. Which of the below mentioned options cannot be the
correct IP address (private IP. assigned to an instance in the public or private subnet?

1. 20.0.0.255
2. 20.0.0.132
3. Access Mostly Uused Products by 50000+ Subscribers
4. 20.0.0.55
Question : A user has launched an EBS backed EC instance. The user has rebooted the instance. Which of the below mentioned statements is not true with
respect to the reboot action?

1. The private and public address remains the same
2. The Elastic IP remains associated with the instance
3. Access Mostly Uused Products by 50000+ Subscribers
4. The instance runs on a new host computer
Ans : 4
Exp : A user can reboot an EC2 instance using the AWS console, the Amazon EC2 CLI or the Amazon EC2 API. Rebooting an instance is equivalent to
rebooting an operating system. However, it is recommended that the user use the Amazon EC2 to reboot the instance instead of running the
operating system reboot command from the instance. The instance remains on the same host computer and maintains its public DNS name,
private IP address, and any data on its instance store volumes. It typically takes a few minutes for the reboot to complete, but the time it takes to
reboot depends on the instance configuration.
Question : A user has setup a web application on EC. The user is generating a log of the application performance at every second. There are multiple
entries for each second. If the user wants to send that data to CloudWatch every minute, what should he do?

1. The user should send only the data of the 60th second as CloudWatch will map the receive data
timezone with the sent data timezone
2. It is not possible to send the custom metric to CloudWatch every minute
3. Access Mostly Uused Products by 50000+ Subscribers
4. Calculate the average of one minute and send the data to CloudWatch
Ans : 3
Exp : Amazon CloudWatch aggregates statistics according to the period length that the user has specified while
getting data from CloudWatch. The user can publish as many data points as he wants with the same or similartime stamps. CloudWatch
aggregates them by the period length when the user calls get statistics about those data points. CloudWatch records the average (sum of all items
divided by the number of items. of the values received for every 1-minute period, as well as the number of samples, maximum value, and minimum
value for the same time period. CloudWatch will aggregate all the data which have time stamps within a one-minute period.
Question : An AWS root account owner is trying to create a policy to access RDS. Which of the below mentioned
statements is true with respect to the above information?

1. Create a policy which allows the users to access RDS and apply it to the RDS instances
2. The user cannot access the RDS database if he is not assigned the correct IAM policy
3. Access Mostly Uused Products by 50000+ Subscribers
4. The policy should be created for the user and provide access for RDS
Ans : 3
Exp : AWS Identity and Access Management is a web service which allows organizations to manage users and user permissions for various AWS
services. If the account owner wants to create a policy for RDS, the owner has to create an IAM user and define the policy which entitles the IAM
user with various RDS services such as Launch Instance, Manage security group, Manage parameter group etc.
Question : A user is using a small MySQL RDS DB. The user is experiencing high latency due to the Multi AZ feature.Which of the below mentioned options
may not help the user in this situation?

1. Schedule the automated back up in non-working hours
2. Use a large or higher size instance
3. Access Mostly Uused Products by 50000+ Subscribers
4. Take a snapshot from standby Replica