AWS Certified SysOps Administrator - Associate Questions and Answers (Dumps and Practice Questions)
Question : A user is measuring the CPU utilization of a private data centre machine every minute. The machine provides the aggregate of data every hour,
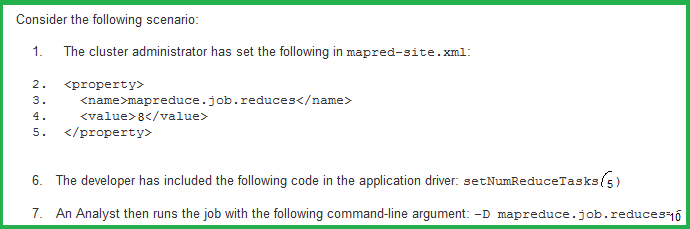
such as Sum of data", "Min value", "Max value, and "Number of Data points".
The user wants to send these values to CloudWatch. How can the user achieve this?

1. Send the data using the put-metric-data command with the aggregate-values parameter
2. Send the data using the put-metric-data command with the average-values parameter
3. Access Mostly Uused Products by 50000+ Subscribers
4. Send the data using the put-metric-data command with the aggregate -data parameter
Correct Answer : Get Lastest Questions and Answer :
Exp: AWS CloudWatch supports the custom metrics. The user can always capture the custom data and upload the data to CloudWatch using CLI or
APIs. The user can publish the data to CloudWatch as single data points or as an aggregated set of data points called a statistic set using the
command put-metric-data. When sending the aggregate data, the user needs to send it with the parameter statistic-values:
awscloudwatch put-metric-data --metric-name (Name) --namespace (Custom namespace) -- timestamp
(UTC Format) --statistic-values Sum=XX,Minimum=YY,Maximum=AA,SampleCount=BB --unit Milliseconds
Question : A user has enabled detailed CloudWatch monitoring with the AWS Simple Notification Service. Which of the below mentioned statements helps
the user understand detailed monitoring better?

1. SNS will send data every minute after configuration
2. There is no need to enable since SNS provides data every minute
3. Access Mostly Uused Products by 50000+ Subscribers
4. SNS cannot provide data every minute
Correct Answer : Get Lastest Questions and Answer :
Exp: CloudWatch is used to monitor AWS as well as the custom services. It provides either basic or detailed
monitoring for the supported AWS products. In basic monitoring, a service sends data points to CloudWatch every five minutes, while in detailed
monitoring a service sends data points to CloudWatch every minute. The AWS SNS service sends data every 5 minutes. Thus, it supports only the
basic monitoring. The user cannot enable detailed monitoring with SNS.
Question : A user has setup a VPC with CIDR .../. The VPC has a private subnet .../. and a public
subnet 20.0.0.0/24.. The user's data centre has CIDR of 20.0.54.0/24 and 20.1.0.0/24. If the private subnet wants to communicate with the data
centre, what will happen?
1. It will allow traffic communication on both the CIDRs of the data centre
2. It will not allow traffic with data centre on CIDR 20.1.0.0/24 but allows traffic communication on 20.0.54.0/24
3. Access Mostly Uused Products by 50000+ Subscribers
4. It will allow traffic with data centre on CIDR 20.1.0.0/24 but does not allow on 20.0.54.0/24
Correct Answer : Get Lastest Questions and Answer :
VPC allows the user to set up a connection between his VPC and corporate or home network data centre. If the user has an IP address prefix in
the VPC that overlaps with one of the networks' prefixes, any traffic to the network's prefix is dropped. In this case CIDR 20.0.54.0/24 falls in the
VPC's CIDR range of 20.0.0.0/16. Thus, it will not allow traffic on that IP. In the case of 20.1.0.0/24, it does not fall in the VPC's CIDR range. Thus,
traffic will be allowed on it.
Related Questions
Question : What is the below command implies
aws cloudwatch put-metric-alarm --alarm-name ec2billing --comparison-operator GreaterThanOrEqualToThreshold --evaluation-periods 1
--metric-name EstimatedCharges --namespace AWS/Billing --dimensions Name=Currency,Value=USD" --period 21600 --statistic Maximum
--threshold 50 --actions-enabled --alarm-actions arn:aws:sns:us-east-1:111111111111:NotifyMe

1. creates an alarm that will send an email message when your estimated month-to-date charges for Amazon EC2 exceed $50.
2. creates an alarm that will send an email message when your estimated month-to-date charges for Amazon EC2 exceed $50 for consecutive 3 months.
3. Access Mostly Uused Products by 50000+ Subscribers
Question : In the Amazon Elastic Compute Cloud (Amazon EC) console
you have setup the Alarm as given setting, what would it implies
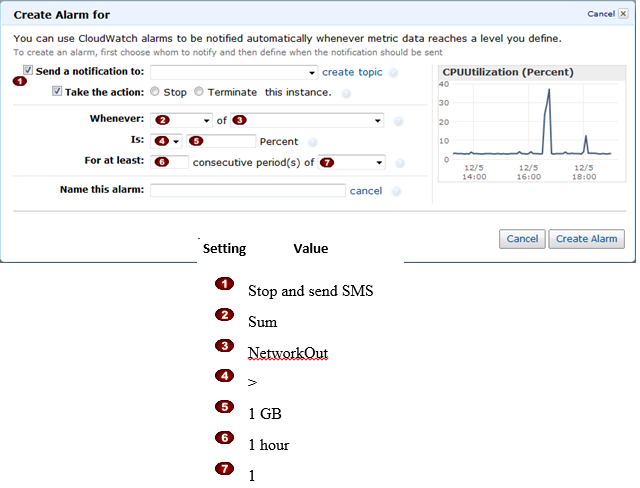
1. Create an alarm that stops an instance and send a text message (SMS) if outbound traffic exceeds 1 GB per hour.
2. Create an alarm that terminates an instance and send a text message (SMS) if outbound traffic exceeds 1 GB per hour.
3. Access Mostly Uused Products by 50000+ Subscribers
Question : In the Amazon Elastic Compute Cloud (Amazon EC) console
you have setup the Alarm as given setting, what would it implies
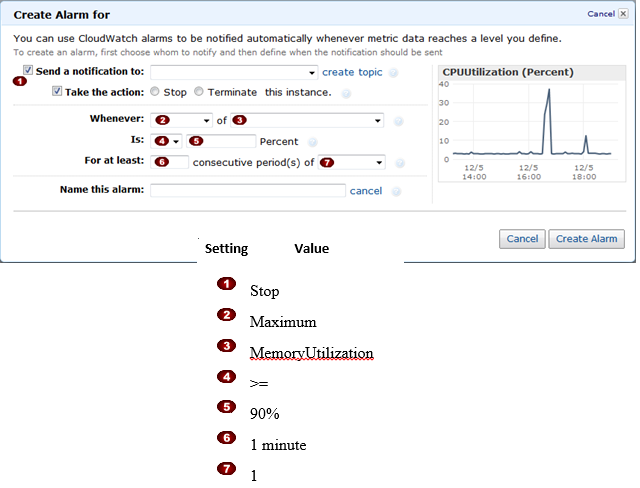
1. Create an alarm that stops an instance when cpu utilization reaches or exceeds 90%, so that application logs can be retrieved for troubleshooting.
2. Create an alarm that stops an instance when memory utilization reaches or exceeds 90%, so that application logs can be retrieved for troubleshooting.
3. Access Mostly Uused Products by 50000+ Subscribers
Question : In the Amazon Elastic Compute Cloud (Amazon EC) console
you have setup the Alarm as given setting, what would it implies
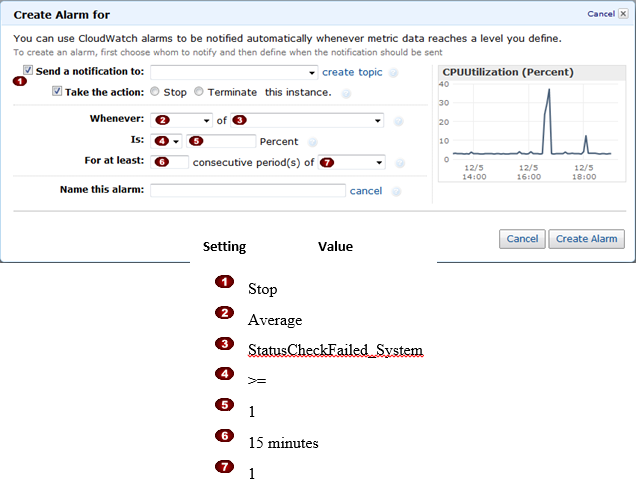
1. Create an alarm that stops an instance that fails three consecutive status checks (performed at 5-minute intervals).
2. Create an alarm that stops an instance that fails three consecutive status checks
3. Access Mostly Uused Products by 50000+ Subscribers
Question : A user has stored data on an encrypted EBS volume. The user wants to share the data with his friend's AWS account. How can user achieve this?

1. Create an AMI from the volume and share the AMI
2. Copy the data to an unencrypted volume and then share
3. Access Mostly Uused Products by 50000+ Subscribers
4. If both the accounts are using the same encryption key then the user can share the volume directly
Ans : 2
Exp : AWS EBS supports encryption of the volume. It also supports creating volumes from existing snapshots
provided the snapshots are created from encrypted volumes. If the user is having data on an encrypted volume and is trying to share it with others,
he has to copy the data from the encrypted volume to a new unencrypted volume. Only then can the user share it as an encrypted volume data.
Otherwise the snapshot cannot be shared.
Question : A user has enabled the Multi AZ feature with the MS SQL RDS database server. Which of the below
mentioned statements will help the user understand the Multi AZ feature better?

1. In a Multi AZ, AWS runs two DBs in parallel and copies the data asynchronously to the replica copy
2. In a Multi AZ, AWS runs two DBs in parallel and copies the data synchronously to the replica copy
3. Access Mostly Uused Products by 50000+ Subscribers
4. AWS MS SQL does not support the Multi AZ feature
Ans : 3
Exp : Amazon RDS provides high availability and failover support for DB instances using Multi-AZ deployments. In a Multi-AZ deployment, Amazon RDS
automatically provisions and maintains a synchronous standby replica in a different Availability Zone. The primary DB instance is synchronously
replicated across Availability Zones to a standby replica to provide data redundancy, eliminate I/O freezes, and minimize latency spikes during
system backups. Running a DB instance with high availability can enhance availability during planned system maintenance, and help protect your
databases against DB instance failure and Availability Zone disruption.Note that the high-availability feature is not a scaling solution for read-only
scenarios; you cannot use a standby replica to serve read traffic. To service read-only traffic, you should use a read replica.
Question : An organization is using cost allocation tags to find the cost distribution of different departments and projects. One of the instances has two
separate tags with the key/ value as "InstanceName/HR", "CostCenter/HR". What will AWS do in this case?

1. InstanceName is a reserved tag for AWS. Thus, AWS will not allow this tag
2. AWS will not allow the tags as the value is the same for different keys
3. Access Mostly Uused Products by 50000+ Subscribers
4. AWS will allow both the tags and show properly in the cost distribution report
Ans : 4
Exp : AWS provides cost allocation tags to categorize and track the AWS costs. When the user applies tags to his AWS resources, AWS generates a
cost allocation report as a comma-separated value (CSV file. with the usage and costs aggregated by those tags. Each tag will have a key-value
and can be applied to services, such as EC2, S3, RDS, EMR, etc. It is required that the key should be different for each tag. The value can be the
same for different keys. In this case since the value is different, AWS will properly show the distribution report with the correct values.
Question : A user is publishing custom metrics to CloudWatch. Which of the below mentioned statements will help the user understand the functionality
better?

1. The user can use the CloudWatch Import tool
2. The user should be able to see the data in the console after around 15 minutes
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user can view as well as upload data using the console, CLI and APIs
Ans : 2
Exp : AWS CloudWatch supports the custom metrics. The user can always capture the custom data and upload the data to CloudWatch using CLI or
APIs. The user has to always include the namespace as a part of the request. However, the other parameters are optional. If the user has
uploaded data using CLI, he can view it as a graph inside the console. The data will take around 2 minutes to upload but can be viewed only after
around 15 minutes.
Question : A user is launching an EC instance in the US East region. Which of the below mentioned options is
recommended by AWS with respect to the selection of the availability zone?

1. Always select the US-East-1-a zone for HA
2. Do not select the AZ; instead let AWS select the AZ
3. Access Mostly Uused Products by 50000+ Subscribers
4. Always select the AZ while launching an instance
Ans : 2
Exp :
When launching an instance with EC2, AWS recommends not to select the availability zone (AZ..
AWS specifies that the default Availability Zone should be accepted. This is because it enables AWS to select the best Availability Zone based on the
system health and available capacity. If the user launches additional instances, only then an Availability Zone should be specified. This is to
specify the same or different AZ from the running instances.
Question : A user has created a VPC with CIDR .../ with only a private subnet and VPN connection using the VPC wizard. The user wants to connect
to the instance in a private subnet over SSH. How should the user define the security rule for SSH?

1. Allow Inbound traffic on port 22 from the user's network
2. The user has to create an instance in EC2 Classic with an elastic IP and configure the security group
of a private subnet to allow SSH from that elastic IP
3. Access Mostly Uused Products by 50000+ Subscribers
4. Allow Inbound traffic on port 80 and 22 to allow the user to connect to a private subnet over the Internet
Ans : 1
Exp : The user can create subnets as per the requirement within a VPC. If the user wants to connect VPC from his own data centre, the user can setup
a case with a VPN only subnet (private. which uses VPN access to connect with his data centre. When the user has configured this setup with
Wizard, all network connections to the instances in the subnet will come from his data centre. The user has to configure the security group of the
private subnet which allows the inbound traffic on SSH (port 22. from the data centre's network range.
Question : A user has created an ELB with the availability zone US-East-A. The user wants to add more zones to ELB to achieve High Availability. How can
the user add more zones to the existing ELB?

1. It is not possible to add more zones to the existing ELB
2. The only option is to launch instances in different zones and add to ELB
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user can add zones on the fly from the AWS console
Ans : 4
Exp : The user has created an Elastic Load Balancer with the availability zone and wants to add more zones to the existing ELB. The user can do so in
two ways:
From the console or CLI, add new zones to ELB;
Launch instances in a separate AZ and add instances to the existing ELB.
Question : A user has configured an Auto Scaling group with ELB. The user has enabled detailed CloudWatch monitoring on Elastic Load balancing. Which
of the below mentioned statements will help the user understand this functionality better?

1. ELB sends data to CloudWatch every minute only and does not charge the user
2. ELB will send data every minute and will charge the user extra
3. Access Mostly Uused Products by 50000+ Subscribers
4. It is not possible to setup detailed monitoring for ELB
Ans : 1
Exp : CloudWatch is used to monitor AWS as well as the custom services. It provides either basic or detailed
monitoring for the supported AWS products. In basic monitoring, a service sends data points to CloudWatch every five minutes, while in detailed
monitoring a service sends data points to CloudWatch every minute. Elastic Load Balancing includes 10 metrics and 2 dimensions, and sends
data to CloudWatch every minute. This does not cost extra.
Question : A user has configured ELB with two EBS backed EC instances. The user is trying to understand the DNS access and IP support for ELB. Which
of the below mentioned statements may not help the user understand the IP mechanism supported by ELB?

1. The client can connect over IPV4 or IPV6 using Dualstack
2. ELB DNS supports both IPV4 and IPV6
3. Access Mostly Uused Products by 50000+ Subscribers
4. The ELB supports either IPV4 or IPV6 but not both
Ans : 4
Exp : Elastic Load Balancing supports both Internet Protocol version 6 (IPv6. and Internet Protocol version 4 (IPv4.. Clients can connect to the user's
load balancer using either IPv4 or IPv6 (in EC2- Classic. DNS. However, communication between the load balancer and its back-end instances
uses only IPv4. The user can use the Dualstack-prefixed DNS name to enable IPv6 support for communications between the client and the load
balancers. Thus, the clients are able to access the load balancer using either IPv4 or IPv6 as their individual connectivity needs dictate.
Question : A user has received a message from the support team that an issue occurred week back between AM to AM and the EC server was not
reachable. The user is checking the CloudWatch metrics of that instance. How can the user find the data easily using the CloudWatch console?

1. The user can find the data by giving the exact values in the time Tab under CloudWatch metrics
2. The user can find the data by filtering values of the last 1 week for a 1 hour period in the Relative tab under CloudWatch metrics
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user can find the data by giving the exact values in the Absolute tab under CloudWatch metrics
Ans : 4
Exp : If the user is viewing the data inside the CloudWatch console, the console provides options to filter values
either using the relative period, such as days /hours or using the Absolute tab where the user can provide data with a specific date and time. The
console also provides the option to search using the local timezone under the time range caption in the console.
Question : A user has setup Auto Scaling with ELB on the EC instances. The user wants to configure that whenever the CPU utilization is below %, Auto
Scaling should remove one instance. How can the user configure this?

1. The user can get an email using SNS when the CPU utilization is less than 10%. The user can use
the desired capacity of Auto Scaling to remove the instance
2. Use CloudWatch to monitor the data and Auto Scaling to remove the instances using scheduled actions
3. Access Mostly Uused Products by 50000+ Subscribers
utilization is less than 10% and configure the Auto Scaling policy to remove the instance
4. Configure CloudWatch to send a notification to the Auto Scaling group when the CPU Utilization is
less than 10% and configure the Auto Scaling policy to remove the instance
Ans : 4
Exp : Amazon CloudWatch alarms watch a single metric over a time period that the user specifies and performs one or more actions based on the value
of the metric relative to a given threshold over a number of time periods. The user can setup to receive a notification on the Auto Scaling group
with the CloudWatch alarm when the CPU utilization is below a certain threshold. The user can configure the Auto Scaling policy to take action for
removing the instance. When the CPU utilization is below 10% CloudWatch will send an alarm to the Auto Scaling group to execute the policy.
Question : A user has enabled detailed CloudWatch metric monitoring on an Auto Scaling group. Which of the below
mentioned metrics will help the user identify the total number of instances in an Auto Scaling group cluding pending, terminating and running
instances?

1. GroupTotalInstances
2. GroupSumInstances
3. Access Mostly Uused Products by 50000+ Subscribers
number of running, terminating and pending instances and sum it
4. GroupInstancesCount
Ans : 1
Exp : CloudWatch is used to monitor AWS as well as the custom services. For Auto Scaling, CloudWatch provides various metrics to get the group
information, such as the Number of Pending, Running or Terminating instances at any moment. If the user wants to get the total number of
Running, Pending and Terminating instances at any moment, he can use the GroupTotalInstances metric.
Question : A user is trying to configure the CloudWatch billing alarm. Which of the below mentioned steps should be
performed by the user for the first time alarm creation in the AWS Account Management section?

1. Enable Receiving Billing Reports
2. Enable Receiving Billing Alerts
3. Access Mostly Uused Products by 50000+ Subscribers
4. Enable CloudWatch Billing Threshold
Ans : 2
Exp : AWS CloudWatch supports enabling the billing alarm on the total AWS charges. Before the user can create an alarm on the estimated charges, he
must enable monitoring of the estimated AWS charges, by selecting the option "Enable receiving billing alerts". It takes about 15 minutes before
the user can view the billing data. The user can then create the alarms.
Question : A user is checking the CloudWatch metrics from the AWS console. The user notices that the CloudWatch data is coming in UTC. The user wants
to convert the data to a local time zone. How can the user perform this?

1. In the CloudWatch dashboard the user should set the local timezone so that CloudWatch shows the
data only in the local time zone
2. In the CloudWatch console select the local timezone under the Time Range tab to view the data as
per the local timezone
3. Access Mostly Uused Products by 50000+ Subscribers
4. The user should have send the local timezone while uploading the data so that CloudWatch will show
the data only in the local timezone
Ans : 2
Exp : If the user is viewing the data inside the CloudWatch console, the console provides options to filter values
either using the relative period, such as days/hours or using the Absolute tab where the user can provide data with a specific date and time. The
console also provides the option to search using the local timezone under the time range caption in the console because the time range tab allows
the user to change the time zone.
Question : An organization (Account ID . has attached the below mentioned IAM policy to a user. What does this policy statement entitle the
user to perform?
"Statement": [
{
"Sid": "AllowUsersAllActionsForCredentials",
"Effect": "Allow",
"Action": [
"iam:*AccessKey*",
],
"Resource": ["arn:aws:iam:: 123412341234:user/${aws:username}"]
}
]
Explanation:
AWS Identity and Access Management is a web service which allows organizations to manage users and user permissions for various AWS
services. If the organization (Account ID 123412341234. wants some of their users to manage keys (access and secret access keys. of all IAM
users, the organization should set the below mentioned policy which entitles the IAM user to modify keys of all IAM users with CLI, SDK or API.
"Statement": [
{
"Sid": "AllowUsersAllActionsForCredentials",
"Effect": "Allow",
"Action": [
"iam:*AccessKey*",
],
"Resource": ["arn:aws:iam:: 123412341234:user/${aws:username}"] }
]

1.
2.
3. Access Mostly Uused Products by 50000+ Subscribers
4.
Ans : 3
Exp :
Question : A user is trying to connect to a running EC instance using SSH. However, the user gets a connection time out error. Which of the below
mentioned options is not a possible reason for rejection?

1. The access key to connect to the instance is wrong
2. The security group is not configured properly
3. Access Mostly Uused Products by 50000+ Subscribers
4. The instance CPU is heavily loaded
Ans : 1
Exp : ISCHANGED Description: If the user is trying to connect to a Linux EC2 instance and receives the connection time out error the probable reasons are:
Security group is not configured with the SSH port
The private key pair is not right
The user name to login is wrong
The instance CPU is heavily loaded, so it does not allow more connections
Question : A user has configured Elastic Load Balancing by enabling a Secure Socket Layer (SSL.
negotiation
configuration known as a Security Policy. Which of the below mentioned options is not part of this secure policy while negotiating the SSL
connection between the user and the client?

1. SSL Protocols
2. Client Order Preference
3. Access Mostly Uused Products by 50000+ Subscribers
4. Server Order Preference
Ans : 2
Exp : Elastic Load Balancing uses a Secure Socket Layer (SSL. negotiation configuration which is known as a
Security Policy. It is used to negotiate the SSL connections between a client and the load balancer. A security policy is a combination of SSL
Protocols, SSL Ciphers, and the Server Order Preference option.
Question : A user has configured CloudWatch monitoring on an EBS backed EC instance. If the user has not attached any additional device, which of the
below mentioned metrics will always show a 0 value?

1. DiskReadBytes
2. NetworkIn
3. Access Mostly Uused Products by 50000+ Subscribers
4. CPUUtilization
Ans : 1
Exp : CloudWatch is used to monitor AWS as the well custom services. For EC2 when the user is monitoring the EC2 instances, it will capture the 7
Instance level and 3 system check parameters for the EC2 instance. Since this is an EBS backed instance, it will not have ephermal storage
attached to it. Out of the 7 EC2 metrics, the 4 metrics DiskReadOps, DiskWriteOps, DiskReadBytes and DiskWriteBytes are disk related data and
available only when there is ephermal storage attached to an instance. For an EBS backed instance without any additional device, this data will be
0.
Question A user has launched an EBS backed EC instance. What will be the difference while performing the restart or stop/start options on that instance?

1. For restart it does not charge for an extra hour, while every stop/start it will be charged as a separate hour
2. Every restart is charged by AWS as a separate hour, while multiple start/stop actions during a single hour will be counted as a single hour
3. Access Mostly Uused Products by 50000+ Subscribers
4. For restart it charges extra only once, while for every stop/start it will be charged as a separate hour
Ans : 1
Exp : For an EC2 instance launched with an EBS backed AMI, each time the instance state is changed from stop to start/ running, AWS charges a full
instance hour, even if these transitions happen multiple times within a single hour. Anyway, rebooting an instance AWS does not charge a new
instance billing hour.
Question : A user has created a queue named "myqueue" in US-East region with AWS SQS. The user's AWS account ID is . If the user wants
to perform some action on this queue, which of the below Queue URL should he use?

1. http://sqs.us-east-1.amazonaws.com/123456789012/myqueue
2. http://sqs.amazonaws.com/123456789012/myqueue
3. Access Mostly Uused Products by 50000+ Subscribers
4. http:// 123456789012.sqs. us-east-1.amazonaws.com/myqueue
Ans : 1
Exp : When creating a new queue in SQS, the user must provide a queue name that is unique within the scope of all queues of user's account. If the
user creates queues using both the latest WSDL and a previous version, he will have a single namespace for all his queues. Amazon SQS
assigns each queue created by user an identifier called a queue URL, which includes the queue name and other components that Amazon SQS
determines. Whenever the user wants to perform an action on a queue, he must provide its queue URL. The queue URL for the account id
123456789012 & queue name "myqueue" in US-East-1 region will be http:// sqs.us-east- 1.amazonaws.com/123456789012/myqueue.
Question : A sys admin is trying to understand the Auto Scaling activities. Which of the below mentioned processes is not performed by Auto Scaling?

1. Reboot Instance
2. Schedule Actions
3. Access Mostly Uused Products by 50000+ Subscribers
4. Availability Zone Balancing
Ans : 1
Exp : There are two primary types of Auto Scaling processes: Launch and Terminate, which launch or terminat
instances, respectively. Some other actions performed by Auto Scaling are: AddToLoadbalancer, AlarmNotification, HealthCheck, AZRebalance,
ReplaceUnHealthy, and ScheduledActions.
Question : A sys admin is trying to understand EBS snapshots. Which of the below mentioned statements will not be
useful to the admin to understand the concepts about a snapshot?

1. The snapshot is synchronous
2. It is recommended to stop the instance before taking a snapshot for consistent data
3. Access Mostly Uused Products by 50000+ Subscribers
4. The snapshot captures the data that has been written to the hard disk when the snapshot command was executed
Ans : 1
Exp : The AWS snapshot is a point in time backup of an EBS volume. When the snapshot command is executed it will capture the current state of the
data that is written on the drive and take a backup. For a better and consistent snapshot of the root EBS volume, AWS recommends stopping the
instance. For additional volumes it is recommended to unmount the device. The snapshots are asynchronous and incremental.
Question : A root account owner has created an S bucket testmycloud. The account owner wants to allow everyone to upload the objects as well as enforce
that the person who uploaded the object should manage the permission of those objects. Which is the easiest way to achieve this?

1. The root account owner should create a bucket policy which allows the IAM users to upload the object
2. The root account owner should create the bucket policy which allows the other account owners to set
the object policy of that bucket
3. Access Mostly Uused Products by 50000+ Subscribers
4. The root account should create the IAM users and provide them the permission to upload content to
the bucket
Ans : 3
Exp : Each AWS S3 bucket and object has an ACL (Access Control List. associated with it. An ACL is a list of grants identifying the grantee and the
permission granted. The user can use ACLs to grant basic read/write permissions to other AWS accounts. ACLs use an Amazon S3-specific XML
schema. The user cannot grant permissions to other users in his account. ACLs are suitable for specific scenarios. For example, if a bucket owner
allows other AWS accounts to upload objects, permissions to these objects can only be managed using the object ACL by the AWS account that
owns the object.
Question : An organization has setup consolidated billing with different AWS accounts. Which of the below mentioned advantages will organization receive
in terms of the AWS pricing?

1. The consolidated billing does not bring any cost advantage for the organization
2. All AWS accounts will be charged for S3 storage by combining the total storage of each account
3. Access Mostly Uused Products by 50000+ Subscribers
4. The free usage tier for all the 3 accounts will be 3 years and not a single year
Ans : 2
Exp : AWS consolidated billing enables the organization to consolidate payments for multiple Amazon Web Services (AWS. accounts within a single
organization by making a single paying account. For billing purposes, AWS treats all the accounts on the consolidated bill as one account. Some
services, such as Amazon EC2 and Amazon S3 have volume pricing tiers across certain usage dimensions that give the user lower prices when
he uses the service more.
Question : A user has launched two EBS backed EC instances in the US-East-a region. The user wants to change the zone of one of the instances. How
can the user change it?

1. Stop one of the instances and change the availability zone
2. The zone can only be modified using the AWS CLI
3. Access Mostly Uused Products by 50000+ Subscribers
4. Create an AMI of the running instance and launch the instance in a separate AZ
Ans : 4
Exp : With AWS EC2, when a user is launching an instance he can select the availability zone (AZ. at the time of launch. If the zone is not selected,
AWS selects it on behalf of the user. Once the instance is launched, the user cannot change the zone of that instance unless he creates an AMI of
that instance and launches a new instance from it.
Question : A user wants to make so that whenever the CPU utilization of the AWS EC instance is above %, the redlight of his bedroom turns on. Which of
the below mentioned AWS services is helpful for this purpose?
1. AWS CloudWatch + AWS SES
2. AWS CloudWatch + AWS SNS
3. Access Mostly Uused Products by 50000+ Subscribers
4. AWS CloudWatch and a dedicated software turning on the light
Question : An organization has added of his AWS accounts to consolidated billing. One of the AWS accounts has
purchased a Reserved Instance (RI. of a small instance size in the US-East-1a zone. All other AWS accounts are running instances of a small size
in the same zone. What will happen in this case for the RI pricing?

1. Only the account that has purchased the RI will get the advantage of RI pricing
2. One instance of a small size and running in the US-East-1a zone of each AWS account will get the
benefit of RI pricing
3. Access Mostly Uused Products by 50000+ Subscribers
size
4. If there are more than one instances of a small size running across multiple accounts in the same
zone no one will get the benefit of RI
Ans : 3
Exp :AWS consolidated billing enables the organization to consolidate payments for multiple Amazon Web Services (AWS. accounts within a single
organization by making a single paying account. For billing purposes, consolidated billing treats all the accounts on the consolidated bill as one
account. This means that all accounts on a consolidated bill can receive the hourly cost benefit of the Amazon EC2 Reserved Instances
purchased by any other account. In this case only one Reserved Instance has been purchased by one account. Thus, only a single instance from
any of the accounts will get the advantage of RI. AWS will implement the blended rate for each instance if more than one instance is running
concurrently.
Question : An organization is planning to use AWS for different departments. The finance department is responsible to pay for all the accounts. However,
they want the cost separation for each account to map with the right cost centre. How can the finance department achieve this?

1. Create 5 separate accounts and make them a part of one consolidate billing
2. Create 5 separate accounts and use the IAM cross account access with the roles for better management
3. Access Mostly Uused Products by 50000+ Subscribers
4. Create 5 separate IAM groups and add users as per the department's employees