AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : Sometime it ispossible that your customer gateway becomes unavailable, and to protect against a loss of connectivity between QuickTechie.com Inc Geneva
datacenter and AWS VPC, You will set up a second VPN connection to your VPC by using a second customer gateway. By using redundant VPN connections and customer
gateways, you can perform maintenance on one of your customer gateways while traffic continues to flow over the second customer gateway's VPN connection. To
establish redundant VPN connections and customer gateways on your network, you need to set up a second VPN connection. The customer gateway IP address

1. for second VPN connection must be publicly accessible
2. can be the same public IP address that you are using for the first VPN connection.
3. for second VPN connection must be privately accessible
4. 1 and 2
5. 2 and 3
Correct Answer : 1
Explanation:To protect against a loss of connectivity in case your customer gateway becomes unavailable, you can set up a second VPN connection to your VPC by using a
second customer gateway. By using redundant VPN connections and customer gateways, you can perform maintenance on one of your customer gateways while traffic continues to flow over
the second customer gateway's VPN connection. To establish redundant VPN connections and customer gateways on your network, you need to set up a second VPN connection. The customer
gateway IP address for the second VPN connection must be publicly accessible and cant be the same public IP address that you are using for the first VPN connection.
Dynamically routed VPN connections use the Border Gateway Protocol (BGP) to exchange routing information between your customer gateways and the virtual private gateways. Statically
routed VPN connections require you to enter static routes for the network on your side of the customer gateway. BGP-advertised and statically entered route information allow gateways
on both sides to determine which tunnels are available and reroute traffic if a failure occurs. We recommend that you configure your network to use the routing information provided
by BGP (if available) to select an available path. The exact configuration depends on the architecture of your network.
Question : You have created a VPN for your organization and found that tunnel credentials for your VPN connection have been compromised. What you must do ?

1. change the IKE preshared key
2. delete the VPN connection
3. delete the VPC and create new one
4. 1 and 2
5. All 1,2 and 3 are correct
Correct Answer : 4
Explanation: If you believe that the tunnel credentials for your VPN connection have been compromised, you can change the IKE preshared key. To do so, delete the VPN connection, create a
new one using the same virtual private gateway, and configure the new keys on your customer gateway. You also need to confirm that the tunnel's inside and outside addresses match,
because these might change when you recreate the VPN connection. While you perform the procedure, communication with your instances in the VPC stops, but the instances continue to
run uninterrupted. After the network administrator implements the new configuration information, your VPN connection uses the new credentials, and the network connection to your
instances in the VPC resumes.
Important
This procedure requires assistance from your network administrator group.
To change the IKE pre-shared key
Delete the VPN connection. For more information, see Deleting a VPN Connection. You don't need to delete the VPC or the virtual private gateway.
Create a new VPN connection and download the new configuration file. For more information, see Create a VPN Connection and Configure the Customer Gateway.
Question : The device on the AWS side of the VPN connection is the ________________ .

1. virtual private gateway
2. private gateway
3. customer gateway
4. customer gateway's external interface
Correct Answer : 1
Explanation: Provides information to AWS about your VPN customer gateway device. The customer gateway is the appliance at your end of the VPN connection. (The device on
the AWS side of the VPN connection is the virtual private gateway.) You must provide the Internet-routable IP address of the customer gateway's external interface. The IP address
must be static and can't be behind a device performing network address translation (NAT).
For devices that use Border Gateway Protocol (BGP), you can also provide the device's BGP Autonomous System Number (ASN). You can use an existing ASN assigned to your network. If you
don't have an ASN already, you can use a private ASN (in the 64512 - 65534 range).
Amazon EC2 supports all 2-byte ASN numbers in the range of 1 - 65534, with the exception of 7224, which is reserved in the us-east-1 region, and 9059, which is reserved in the
eu-west-1 region.
Related Questions
Question : You have created a subnet and specified the CIDR block .../ for subnet. Please select the correct statement

1. It supports 24 IP addresses, You can break this CIDR block into two subnets, each supporting 12 IP addresses
2. It supports 128 IP addresses, You can break this CIDR block into two subnets, each supporting 64 IP addresses
3. It supports 256 IP addresses, You can break this CIDR block into two subnets, each supporting 128 IP addresses
4. It supports 24 IP addresses, You can not break this CIDR block into two subnets
Question : In the given diagram,
the route table associated with subnet 1 routes
all traffic __________ to an Internet
gateway (for example, igw-1a2b3c4d).
Because instance V1 has an Elastic IP address,
it can be reached from the Internet.
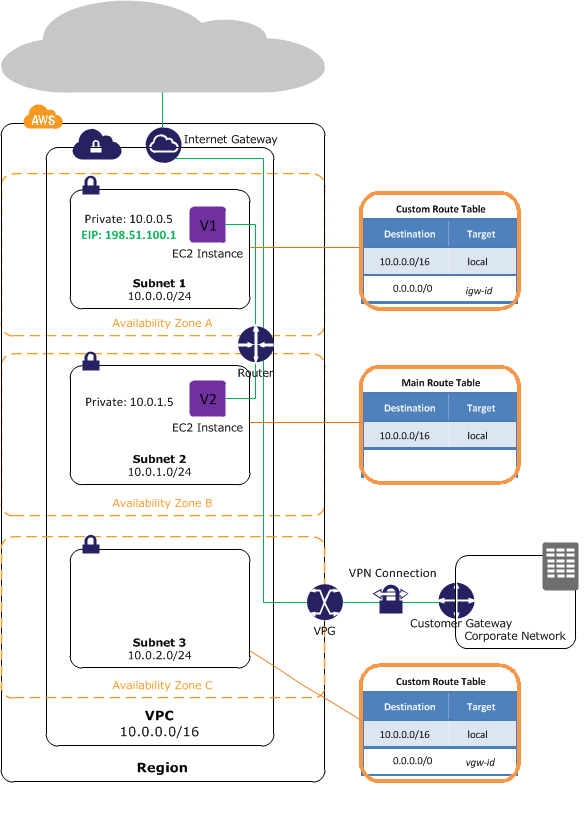
1. (0.0.0.16/0)
2. (0.0.0.24/0)
3. (0.0.0.0/0)
4. (0.0.0.5/0)
Question : QuickTechie.com is planning to implement a scalable web application with AWS EC to achieve HA with multi AZ features. The application requires an
Weblogic J2EE app server and may require a load which will be catered by 2 large instances. Select the configurations is better choice for HA in DR

1. Launch only one large instance and setup Auto Scaling with ELB.
2. Launch two large instances in separate AZs and load balance them with ELB.
3. Launch 8 small EC2 instances with two instances in each zone for better HA and DR and load balance each with ELB.
4. Launch 4 small instances in separate AZs and load balance them with ELB.
Question : You have created a Subnet where all your app servers instances will be launched and the database remain in the local data center. Also you have
created VPN for having communication between your dataceneter and VPC subnets. Now you wish to provide security on instance level under a subnet. Which one
from the below feature will help you to implement the same.

1. Restricting the port 80 and 8080 for outbound traffic.
2. security groups will help
3. Network ACL will help
4. 1 and 3 both needs to be implemented
Question : You are running QuickTechie.com website using servers, ( servers in different data centeres , where is active and is passive).
Now you want to configure DNS such that whenever request for website comes and if any of the active server is available out of 5 active it should not return
the IP address of Passive servers. Which of the following configuration will help implmenting it..

1. Amazon Route 53 , Active-active failover
2. Amazon Route 53 , Active-passive failover
3. Amazon Route 53 , Passive-passive failover
4. Amazon Route 53 ,Active-active-passive
5. Any of the above
Question : QuickTechie.com is setting up Oracle RDS for their applications and wants to secure Oracle RDS access with VPC.
Which of the following options is not required while designing the Oracle RDS with VPC?

1. If the QuickTechie.com Inc is connecting RDS from the internet it must enable the VPC attributes DNS hostnames and DNS resolution.
2. The QuickTechie.com Inc must create a subnet group with public and private subnets. Both the subnets can be in the same or separate AZ.
3. The QuickTechie.com Inc must create a subnet group with VPC using more than one subnets which are a part of separate AZs.
4. The QuickTechie.com Inc should keep minimum one IP address in each subnet reserved for RDS failover.