AWS Certified Solutions Architect - Professional Questions and Answers (Dumps and Practice Questions)
Question : When you are trying to delete default security group, what would happen in AWS VPC

1. Successfully deleted
2. It will be delted, but immediately another default one would be created without any rule.
3. you'll get the following error: Client.CannotDelete: the specified group: "sg-51530134" name: "default" cannot be deleted by a user.
4. Successfully deleted, with warning.
Correct Answer : 3
Explanation: You can change the rules for the default security group.
You can't delete a default security group. If you try to delete the default security group, you'll get the following error: Client.CannotDelete: the specified group: "sg-51530134"
name: "default" cannot be deleted by a user.
Question : AWS VPC automatically comes with a modifiable default network ACL, select the correct statement for this default ACL.

1. it allows all inbound and outbound traffic.
2. it allows all inbound traffic only.
3. it allows all outbound traffic only.
4. it would not allow all inbound and outbound traffic.
Correct Answer : 1
Explanation: The following are the basic things that you need to know about network ACLs:
A network ACL is a numbered list of rules that we evaluate in order, starting with the lowest numbered rule, to determine whether traffic is allowed in or out of any subnet
associated with the network ACL. The highest number that you can use for a rule is 32766. We suggest that you start by creating rules with rule numbers that are multiples of 100,
so that you can insert new rules where you need to later on.
A network ACL has separate inbound and outbound rules, and each rule can either allow or deny traffic.
Your VPC automatically comes with a modifiable default network ACL; by default, it allows all inbound and outbound traffic.
You can create custom network ACLs; each custom network ACL starts out closed (permits no traffic) until you add a rule.
Each subnet must be associated with a network ACL; if you don't explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL.
Network ACLs are stateless; responses to allowed inbound traffic are subject to the rules for outbound traffic (and vice versa).
Question : Consider the following policy definition.
{
"Version": "2012-10-17",
"Statement":[{
"Effect":"Allow",
"Action":["ec2:DescribeVpcs",
"ec2:DescribeSubnets",
"ec2:DescribeInternetGateways",
"ec2:DescribeCustomerGateways",
"ec2:DescribeVpnGateways",
"ec2:DescribeVpnConnections",
"ec2:DescribeRouteTables",
"ec2:DescribeAddresses",
"ec2:DescribeSecurityGroups",
"ec2:DescribeNetworkAcls",
"ec2:DescribeDhcpOptions",
"ec2:DescribeTags",
"ec2:DescribeInstances"],
"Resource":"*"
}
]
}
Select the correct statement which applies.

1. policy grants users permission to list your VPCs and their components. They can create, update, or delete them.
2. policy grants users permission to list your VPCs and their components. They can't create, update, or delete them.
3. policy grants users permission to list your VPCs and their components. They can create, update, but cant delete them.
4. grants users permission to launch instances, stop instances, start instances, terminate instances, and describe the available resources for Amazon EC2 and Amazon VPC.
Correct Answer : 2
Explanation:The policy grants users permission to list your VPCs and their components. They can't create, update, or delete them..
Related Questions
Question :

1. A
2. B
3. Access Mostly Uused Products by 50000+ Subscribers
4. D
Question :
A. AWS Account
B. AWS Service
C. SAML Provider
D. Active Directory Users and Groups
E. Identity Provider

1. A,B
2. B,D
3. Access Mostly Uused Products by 50000+ Subscribers
4. A,C
5. D,E
Question :
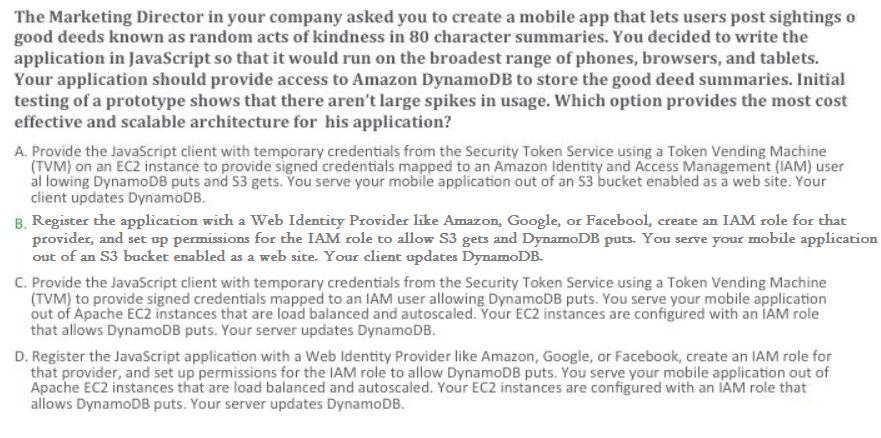
1. A
2. B
3. Access Mostly Uused Products by 50000+ Subscribers
4. D
Question : QuickTechie.com has hosted all the applications in the AWS VPC and his security partner is at a remote place and wants to have access to AWS to view
all the VPC records. How can the organization meet the expectations of the partner without compromising on the security of their AWS infrastructure?

1. The organization should not accept the request as sharing the credentials means compromising on security.
2. Create an IAM user who will have read only access to the AWS VPC and share those credentials with the auditor.
3. Access Mostly Uused Products by 50000+ Subscribers
4. Create an IAM role which will have read only access to all EC2 services including VPC and assign that role to the auditor .
Question : Your corporate headquarters in New York can have an AWS Direct Connect connection to the VPC and your branch offices can use VPN connections to the
VPC. The branch offices in Los Angeles and Miami can send and receive data with each other and with your corporate headquarters, all using the AWS________

1. VPN
2. VPN CloudHub
3. Access Mostly Uused Products by 50000+ Subscribers
4. VNC
Question : Your company hosts an on-premises legacy engineering application with GB of data shared via a central file server. The engineering data consists of
thousands of individual files ranging in size from megabytes to multiple gigabytes. Engineers typically modify 5-10 percent of the files a day. Your CTO would like
to migrate this application to AWS, but only if the application can be migrated over the weekend to minimize user downtime. You calculate that it will take a
minimum of 48 hours to transfer 900GB of data using your company's existing 45-Mbps Internet connection.
After replicating the application's environment in AWS, which option will allow you to move the application's data to AWS without losing any data and within the given timeframe?

1. Copy the data to Amazon S3 using multiple threads and multi-part upload for large files over the weekend, and work in parallel with your developers to reconfigure the
replicated application environment to leverage Amazon S3 to serve the engineering files.
2. Sync the application data to Amazon S3 starting a week before the migration, on Friday morning perform a final sync, and copy the entire data set to your AWS file
server after the sync completes.
3. Access Mostly Uused Products by 50000+ Subscribers
EBS volume, mount the resulting EBS volume to your AWS file server on Sunday.
4. Leverage the AWS Storage Gateway to create a Gateway-Stored volume. On Friday copy the application data to the Storage Gateway volume. After the data has been copied,
perform a snapshot of the volume and restore the volume as an EBS volume to be attached to your AWS file server on Sunday.