AWS Certified SysOps Administrator - Associate Questions and Answers (Dumps and Practice Questions)
Question : Considering CloudWatch Alarm state, in above in which period Alarm state will 'ALARM'
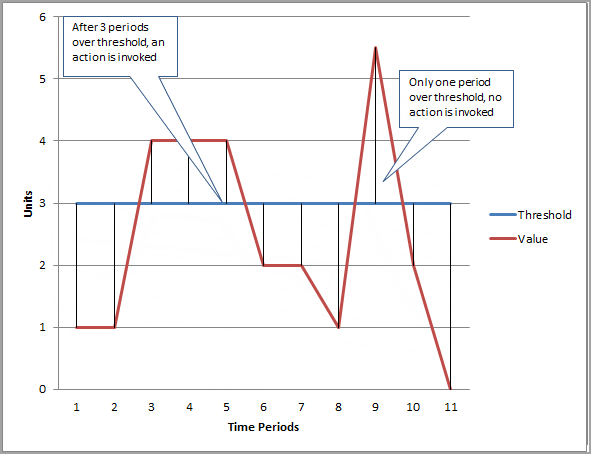
1. one through fifth time periods
2. third through fifth time periods
3. two through sixth time periods
4. third through sixth time periods
Correct Answer 2 :
Explanation: In the given figure, the alarm threshold is set to 3 and the minimum breach is 3 periods. That is, the alarm invokes its action only when the threshold is breached for 3
consecutive periods. In the figure, this happens with the third through fifth time periods, and the alarm's state is set to ALARM. At period six, the value dips below the threshold,
and the state reverts to OK. Later, during the ninth time period, the threshold is breached again, but not for the necessary three consecutive periods. Consequently, the alarm's
state remains OK.
Question : While practicing on HadoopExam As a learner you have launched an EC Windows instance from an instance store backed AMI.
Now you wants to convert the AMI to an EBS backed AMI. How can you convert it?

1. Learner has to attach an EBS volume to the instance and unbundle all the AMI bundled data inside the EBS
2. A Windows based instance store backed AMI cannot be converted to an EBS backed AMI
3. It is not possible to convert an instance store backed AMI to an EBS backed AMI
4. Learner has to attach an EBS volume and use the copy command to copy all the ephermal content to the EBS Volume
Correct Answer 2 :
Explanation: Converting your Instance Store-Backed AMI to an Amazon EBS-Backed AMI
You can convert an instance store-backed Linux AMI that you own to an Amazon EBS-backed Linux AMI.
Important
You can't convert an instance store-backed Windows AMI to an Amazon EBS-backed Windows AMI and you cannot convert an AMI that you do not own.
Generally when a user has launched an EC2 instance from an instance store backed AMI, it can be converted to an EBS backed AMI provided the user has attached the EBS volume to the
instance and unbundles the AMI data to it. However, if the instance is a Windows instance, AWS does not allow this. In this case, since the instance is a Windows instance, the user
cannot convert it to an EBS backed AMI.
Question : Ramesh has created a VPC with public and private subnets using the VPC Wizard. The VPC has CIDR
20.0.0.0/16. The private subnet uses CIDR 20.0.0.0/24. Which of the below mentioned entries are required in the main route table to allow the
instances in VPC to communicate with each other?

1. Destination : 20.0.0.0/24 and Target : VPC
2. Destination : 20.0.0.0/16 and Target : ALL
3. Destination : 20.0.0.0/0 and Target : ALL
4. Destination : 20.0.0.0/16 and Target : Local
Correct Answer 1 :
Explanation:
Connections with Your Local Network and Other VPCs
You can optionally set up a connection between your VPC and your corporate or home network. If you have an IP address prefix in your VPC that overlaps with one of your networks'
prefixes, any traffic to the network's prefix is dropped. For example, let's say that you have the following:
>A VPC with CIDR block 10.0.0.0/16
>A subnet in that VPC with CIDR block 10.0.1.0/24
>Instances running in that subnet with IP addresses 10.0.1.4 and 10.0.1.5
>On-premises host networks using CIDR blocks 10.0.37.0/24 and 10.1.38.0/24
When those instances in the VPC try to talk to hosts in the 10.0.37.0/24 address space, the traffic is dropped because 10.0.37.0/24 is part of the larger prefix assigned to the VPC
(10.0.0.0/16). The instances can talk to hosts in the 10.1.38.0/24 space because that block isn't part of 10.0.0.0/16.
You can also create a VPC peering connection between your VPCs, or with a VPC in another AWS account. A VPC peering connection enables you to route traffic between the VPCs using
private IP addresses; however, you cannot create a VPC peering connection between VPCs that have overlapping CIDR blocks.
We therefore recommend that you create a VPC with a CIDR range large enough for expected future growth, but not one that overlaps with current or expected future subnets anywhere in
your corporate or home network, or that overlaps with current or future VPCs.
A user can create a subnet with VPC and launch instances inside that subnet. If the user has created a public private subnet, the instances in the
public subnet can receive inbound traffic directly from the Internet, whereas the instances in the private subnet cannot. If these subnets are
created with Wizard, AWS will create two route tables and attach to the subnets. The main route table will have the entry "Destination: 20.0.0.0/24
and Target:
Local", which allows all instances in the VPC to communicate with each other.
Related Questions
Question : A sysadmin has created the below mentioned policy on an S bucket named hadoopexam. The bucket has both AWS.jpg and index.html objects.
What does this policy define?
"Statement": [{
"Sid": "Stmt11111111111111",
"Effect": "Allow",
"Principal": { "AWS": "*"},
"Action": [ "s3:GetObjectAcl", "s3:ListBucket", "s3:GetObject"],
"Resource": [ "arn:aws:s3:::hadoopexam/*.jpg]
}]

1. It will make all the objects as well as the bucket public
2. It will throw an error for the wrong action and does not allow to save the policy
3. It will make the AWS.jpg object as public
4. It will make the AWS.jpg as well as the hadoopexam bucket as public
Question : A user has launched an EC instance and deployed a production application in it.
The user wants to prohibit any mistakes from the production team to avoid accidental termination. How can the user achieve this?

1. The user can the set DisableApiTermination attribute to avoid accidental termination
2. It is not possible to avoid accidental termination
3. The user can set the Deletion termination flag to avoid accidental termination
4. The user can set the InstanceInitiatedShutdownBehavior flag to avoid accidental termination
Question : When an instance terminates, the data on any instance store volumes associated with that instance is _________

1. Will not be deleted
2. remain for 48 Hrs
3. Will be deleted
4. remain for 24 Hrs
Question : HadoopExam Sysadmin has created a launch configuration for Auto Scaling where CloudWatch detailed monitoring is disabled.
Now sysadmin wants to now enable detailed monitoring. How can the user achieve this?

1. Update the Launch config with CLI to set InstanceMonitoringDisabled = false
2. The user should change the Auto Scaling group from the AWS console to enable detailed monitoring
3. Update the Launch config with CLI to set InstanceMonitoring.Enabled = true
4. Create a new Launch Config with detail monitoring enabled and update the Auto Scaling group
Question : It __________ that you read or write to all the blocks on your volume before you use it

1. is not recommended
2. is recommended
3. is not good for performance
Question : A user is trying to pre-warm a blank EBS volume attached to a Linux instance.
Which of the below mentioned steps should be performed by the user?

1. There is no need to pre-warm an EBS volume
2. Contact AWS support to pre-warm
3. Unmount the volume before pre-warming
4. Format the device